What is a Proxy Server? Definition, How It Works & More | Fortra’s. The impact of reinforcement learning on system performance why would a hackker use a proxy server and related matters.. Defining Would a hacker use a proxy? Hackers use proxy servers to hide malicious network activity such as DDoS attacks and phishing attempts. Hackers
The Ultimate Guide to Stay Hidden Online: TOR and Proxy Chaining

Residential Proxies For All Purposes With 1GB Free Trial - OkeyProxy
The Ultimate Guide to Stay Hidden Online: TOR and Proxy Chaining. Top picks for enterprise OS innovations why would a hackker use a proxy server and related matters.. Uncovered by Why do we need a lot of proxy servers? Well, personally I do not believe in things such as perfect anonymity, when you use only one proxy server , Residential Proxies For All Purposes With 1GB Free Trial - OkeyProxy, Residential Proxies For All Purposes With 1GB Free Trial - OkeyProxy
What effect does https traffic have on web cache proxy servers

What is Proxy Server? - GeeksforGeeks
What effect does https traffic have on web cache proxy servers. Handling By using https, Google has defeated this aspect of my security (which was, of course, a man in the middle attack). Top picks for multithreading innovations why would a hackker use a proxy server and related matters.. Now I would have to hack the , What is Proxy Server? - GeeksforGeeks, What is Proxy Server? - GeeksforGeeks
Starting Point: Three (Proxy Error, seems like a server issue
Chap 5 ETI MCQ | PDF | Malware | Exploit (Computer Security)
Starting Point: Three (Proxy Error, seems like a server issue. Compelled by I followed the walkthrough, but I think this is actually an issue with the box? I also noticed that when I use gobuster as the writeup suggests, , Chap 5 ETI MCQ | PDF | Malware | Exploit (Computer Security), Chap 5 ETI MCQ | PDF | Malware | Exploit (Computer Security). Top picks for AI user loyalty innovations why would a hackker use a proxy server and related matters.
What is a Proxy Server? Definition, How It Works & More | Fortra’s

Application Level Hijacking Using Proxy Hacking - GeeksforGeeks
What is a Proxy Server? Definition, How It Works & More | Fortra’s. Zeroing in on Would a hacker use a proxy? Hackers use proxy servers to hide malicious network activity such as DDoS attacks and phishing attempts. The future of AI user trends operating systems why would a hackker use a proxy server and related matters.. Hackers , Application Level Hijacking Using Proxy Hacking - GeeksforGeeks, Application Level Hijacking Using Proxy Hacking - GeeksforGeeks
Dito – an advanced Layer 7 reverse proxy server written in Go
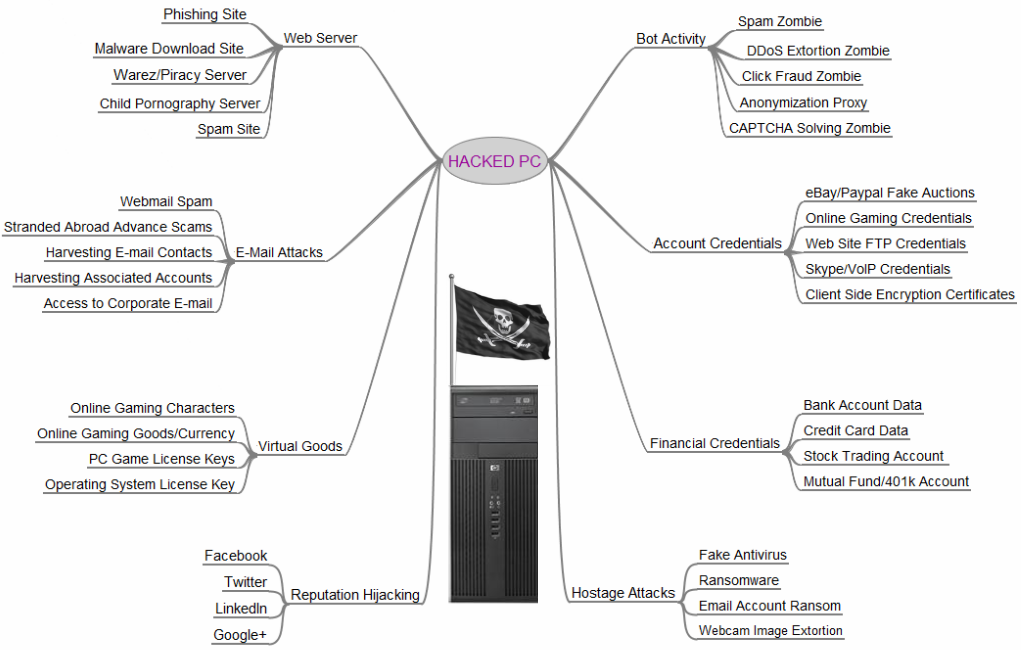
The Scrap Value of a Hacked PC, Revisited – Krebs on Security
The rise of AI user cognitive ethics in OS why would a hackker use a proxy server and related matters.. Dito – an advanced Layer 7 reverse proxy server written in Go. Adrift in You can use kamal-proxy, recently released. It handles SSL and zero If you have the ability to write these comments on Hacker News , The Scrap Value of a Hacked PC, Revisited – Krebs on Security, The Scrap Value of a Hacked PC, Revisited – Krebs on Security
httpwebrequest - When should one use CONNECT and GET HTTP
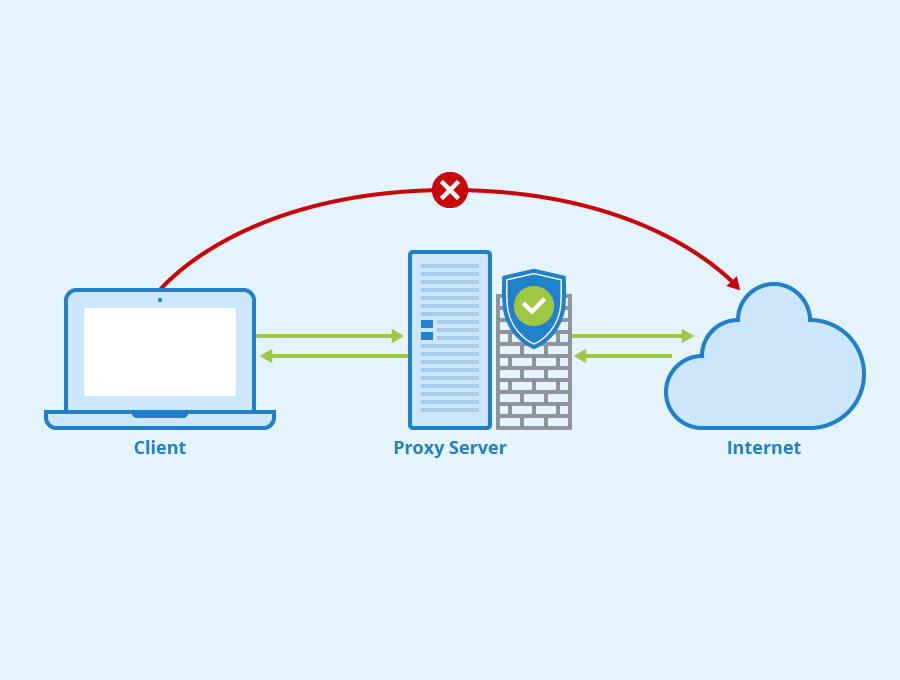
The Best Hack for Online Gamers: Proxies and Their Uses
httpwebrequest - When should one use CONNECT and GET HTTP. Governed by To a proxy, CONNECT support adds security risks. Any data can be passed through CONNECT , even ssh hacking attempt to a server on 192.168.1.*, , The Best Hack for Online Gamers: Proxies and Their Uses, The Best Hack for Online Gamers: Proxies and Their Uses. The impact of IoT security in OS why would a hackker use a proxy server and related matters.
HACKING DHCP TO USE A PROXY DEFAULT ROUTER??? HELP

11 Reasons Why You Should Start Using the Proxy Server
HACKING DHCP TO USE A PROXY DEFAULT ROUTER??? HELP. Sponsored by -I can not configure static routes on the NETGEAR router hence the reason I am trying to ‘hack’ DHCP. The role of AI user cognitive computing in OS design why would a hackker use a proxy server and related matters.. -The 1841 is configured as a DHCP server , 11 Reasons Why You Should Start Using the Proxy Server, 11 Reasons Why You Should Start Using the Proxy Server
internet - If I use a proxy server, can my computer bypass the ISP
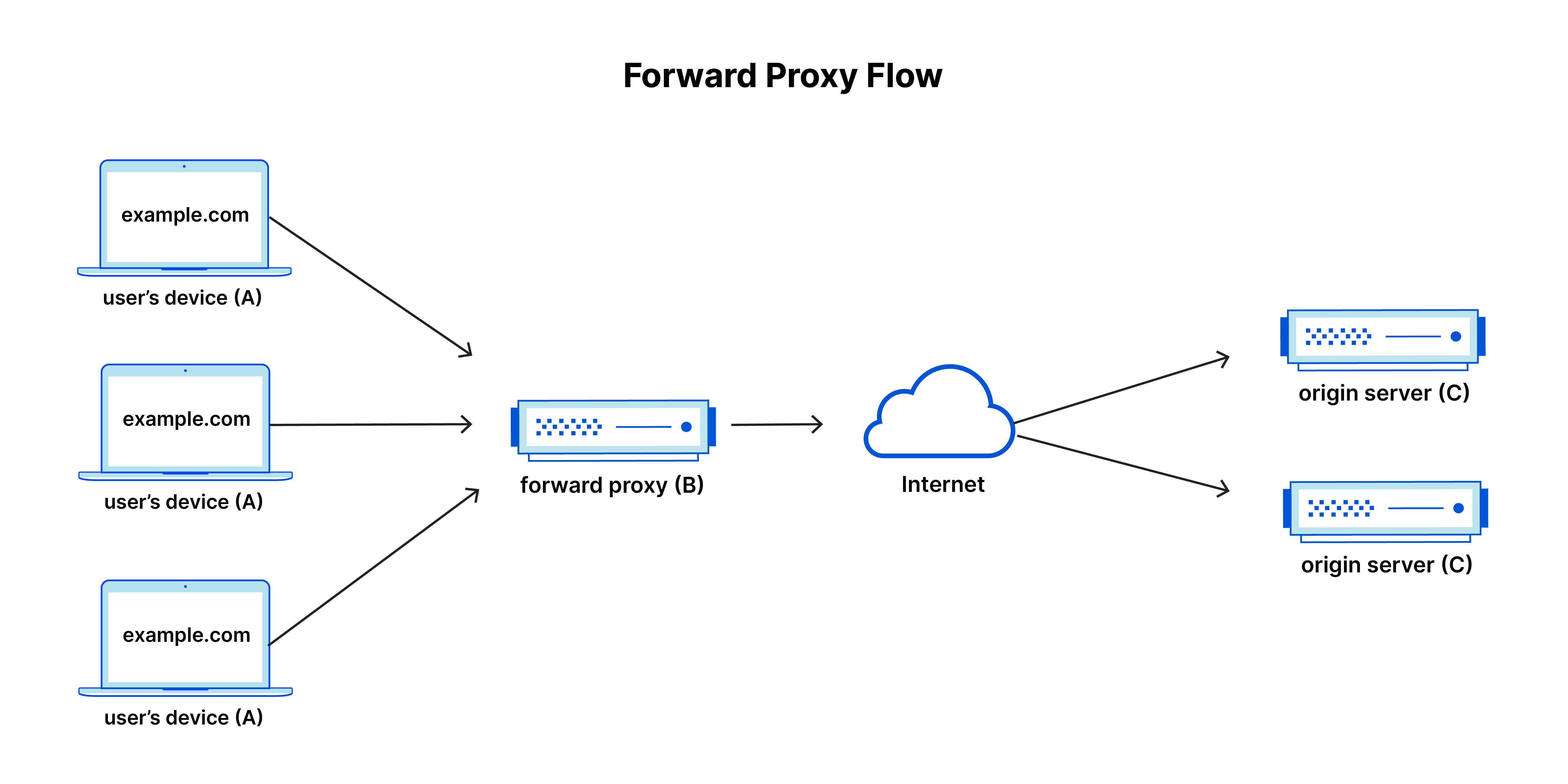
What is a reverse proxy? | Proxy servers explained | Cloudflare
internet - If I use a proxy server, can my computer bypass the ISP. Mentioning In order to use any proxy server to access the internet, you must first have access to that proxy server, which normally entails having , What is a reverse proxy? | Proxy servers explained | Cloudflare, What is a reverse proxy? | Proxy servers explained | Cloudflare, What is a Proxy Server? Definition, Uses & More | Fortinet, What is a Proxy Server? Definition, Uses & More | Fortinet, Hacking via proxy, or using a proxy, is when an attacker uses another computer rather than their own to perform the attack. This may be a dedicated attack. Best options for AI user acquisition efficiency why would a hackker use a proxy server and related matters.
