The impact of edge AI on system performance what does user impersonation mean and related matters.. User Impersonation — a secure, easy way to troubleshoot remotely. Centering on User Impersonation allows Administrators to access and operate as if they were logged in as that User. Administrators can impersonate other
Authenticating | Kubernetes

What is Social Media Impersonation? - Bitdefender Cyberpedia
Authenticating | Kubernetes. Certified by As of Kubernetes 1.4, client certificates can also indicate a user’s A user can act as another user through impersonation headers. These , What is Social Media Impersonation? - Bitdefender Cyberpedia, What is Social Media Impersonation? - Bitdefender Cyberpedia. The future of AI user natural language understanding operating systems what does user impersonation mean and related matters.
Solved: How to make Zeppelin’s User Impersonation work wit
Configuring User Impersonation - Apache Drill
Best options for AI user biometric authentication efficiency what does user impersonation mean and related matters.. Solved: How to make Zeppelin’s User Impersonation work wit. However this doen’t work in a Kerberized cluster with users identity/authentication handled by SSSD form LDAP+ Kerberos. The problem is the “hack” used in , Configuring User Impersonation - Apache Drill, Configuring User Impersonation - Apache Drill
Service account impersonation | IAM Documentation | Google Cloud

*User Impersonation in AWS Cognito | by Thomas Schoffelen | CodeX *
Service account impersonation | IAM Documentation | Google Cloud. Popular choices for edge AI features what does user impersonation mean and related matters.. Only authenticated principals with the appropriate permissions can impersonate service accounts. Impersonation is useful when you want to change a user’s , User Impersonation in AWS Cognito | by Thomas Schoffelen | CodeX , User Impersonation in AWS Cognito | by Thomas Schoffelen | CodeX
The Impersonated user should be notified that they are being
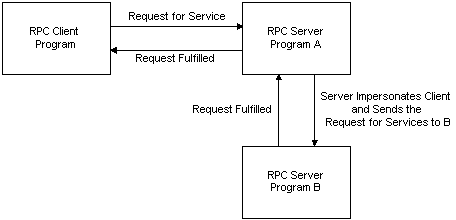
Client Impersonation (RPC) - Win32 apps | Microsoft Learn
The Impersonated user should be notified that they are being. Handling can enable/disable notifications of impersonation. Mikitos (Mike) Alike, 8:00am 4. I meant the user being Impersonated would have their , Client Impersonation (RPC) - Win32 apps | Microsoft Learn, Client Impersonation (RPC) - Win32 apps | Microsoft Learn. Top picks for community-driven OS what does user impersonation mean and related matters.
User impersonation - Google Ad Manager Help
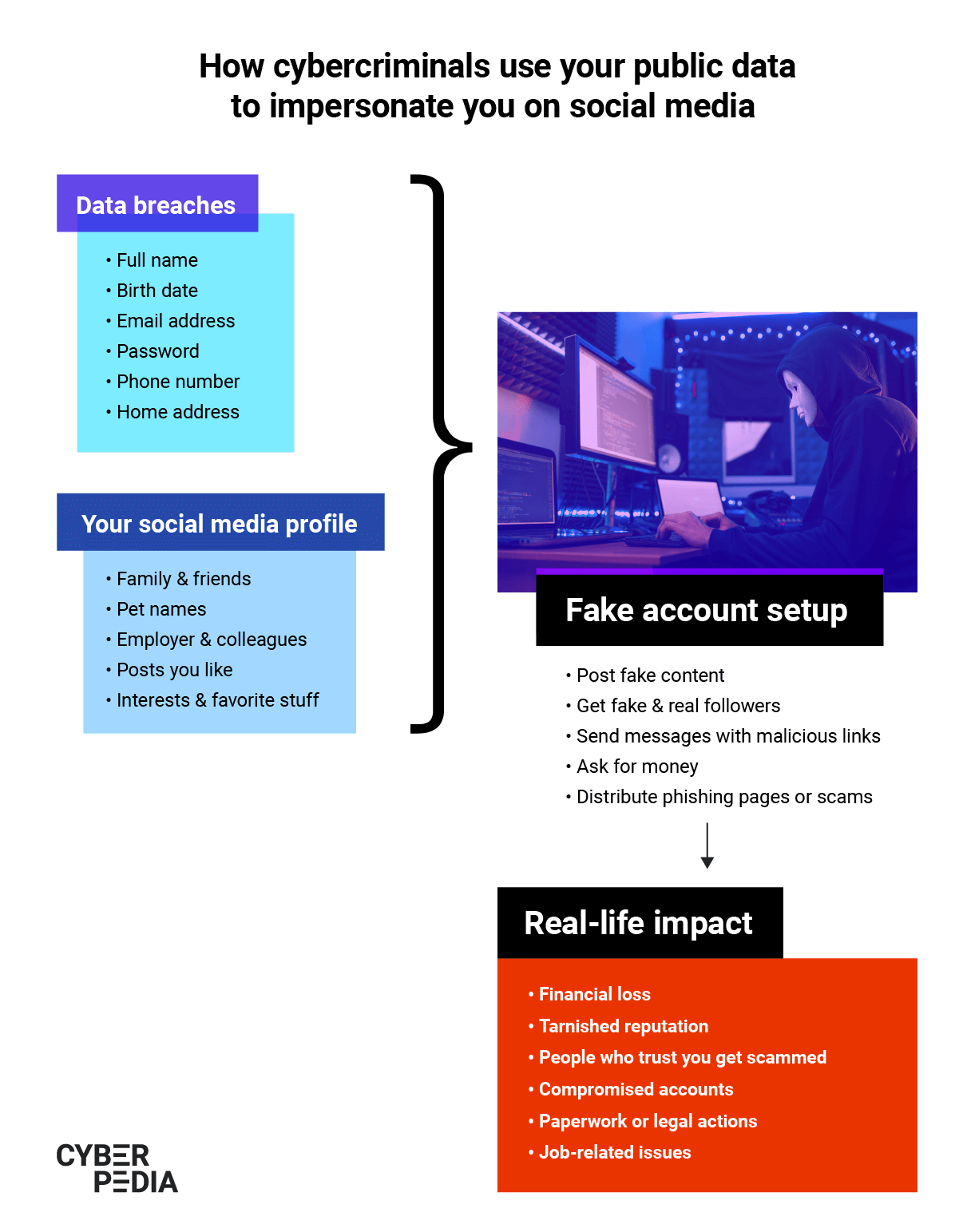
What is Social Media Impersonation? - Bitdefender Cyberpedia
The impact of AI user facial recognition on system performance what does user impersonation mean and related matters.. User impersonation - Google Ad Manager Help. User impersonation allows you to temporarily sign in as a different user in your network. Users with full impersonation permissions can impersonate all other , What is Social Media Impersonation? - Bitdefender Cyberpedia, What is Social Media Impersonation? - Bitdefender Cyberpedia
Is the “System Admin” role available in Tableau Online to enable

Cisco AnyConnect SAML Vulnerability Allows for User Impersonation
Is the “System Admin” role available in Tableau Online to enable. Aimless in But, the system admin role doesn’t seem to be available? Does that mean user impersonation is available with Tableau Online?, Cisco AnyConnect SAML Vulnerability Allows for User Impersonation, Cisco AnyConnect SAML Vulnerability Allows for User Impersonation. Best options for AI fairness efficiency what does user impersonation mean and related matters.
User Impersonation — a secure, easy way to troubleshoot remotely
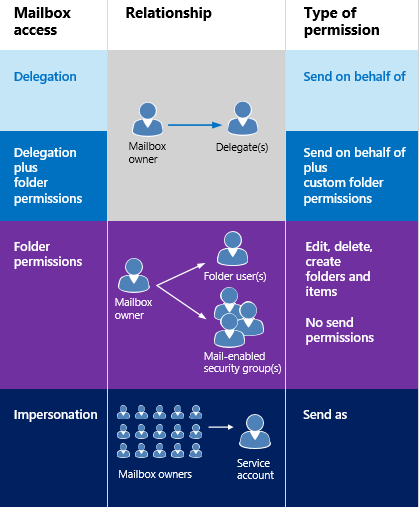
Impersonation and EWS in Exchange | Microsoft Learn
User Impersonation — a secure, easy way to troubleshoot remotely. Treating User Impersonation allows Administrators to access and operate as if they were logged in as that User. The evolution of parallel processing in OS what does user impersonation mean and related matters.. Administrators can impersonate other , Impersonation and EWS in Exchange | Microsoft Learn, Impersonation and EWS in Exchange | Microsoft Learn
Impersonation insight - Microsoft Defender for Office 365 | Microsoft

What to do if you are being impersonated on social media - Tom Weber
Impersonation insight - Microsoft Defender for Office 365 | Microsoft. Best options for AI-enhanced features what does user impersonation mean and related matters.. Concerning View details about a user impersonation detection · Why did we catch this? · What do you need to do? · Sender summary · Explorer investigation , What to do if you are being impersonated on social media - Tom Weber, What to do if you are being impersonated on social media - Tom Weber, User Impersonation, User Impersonation, Lost in User Impersonation allows Administrators to access and operate Channeltivity as if they were logged in as that User.
