Have you ever wondered what lurks in the shadows of the digital world, ready to strike at your precious data? Trojans, the sneaky cyber foes, are just that. Just like their mythological counterparts, these malicious programs disguise themselves as harmless apps or files, waiting for the unsuspecting to click. But fear not, fellow netizens! In this enlightening guide, we’ll unveil the secrets of Trojans, exposing their tactics and empowering you with the knowledge to outwit them. From their deceptive disguises to the telltale signs of an infection, we’ll arm you with the knowledge to protect your digital fortress against these cunning invaders. Join us on this cybersecurity adventure, where we’ll demystify Trojans and safeguard your digital sanctuary.
- Trojans Unmasked: Understanding the Malware Threat
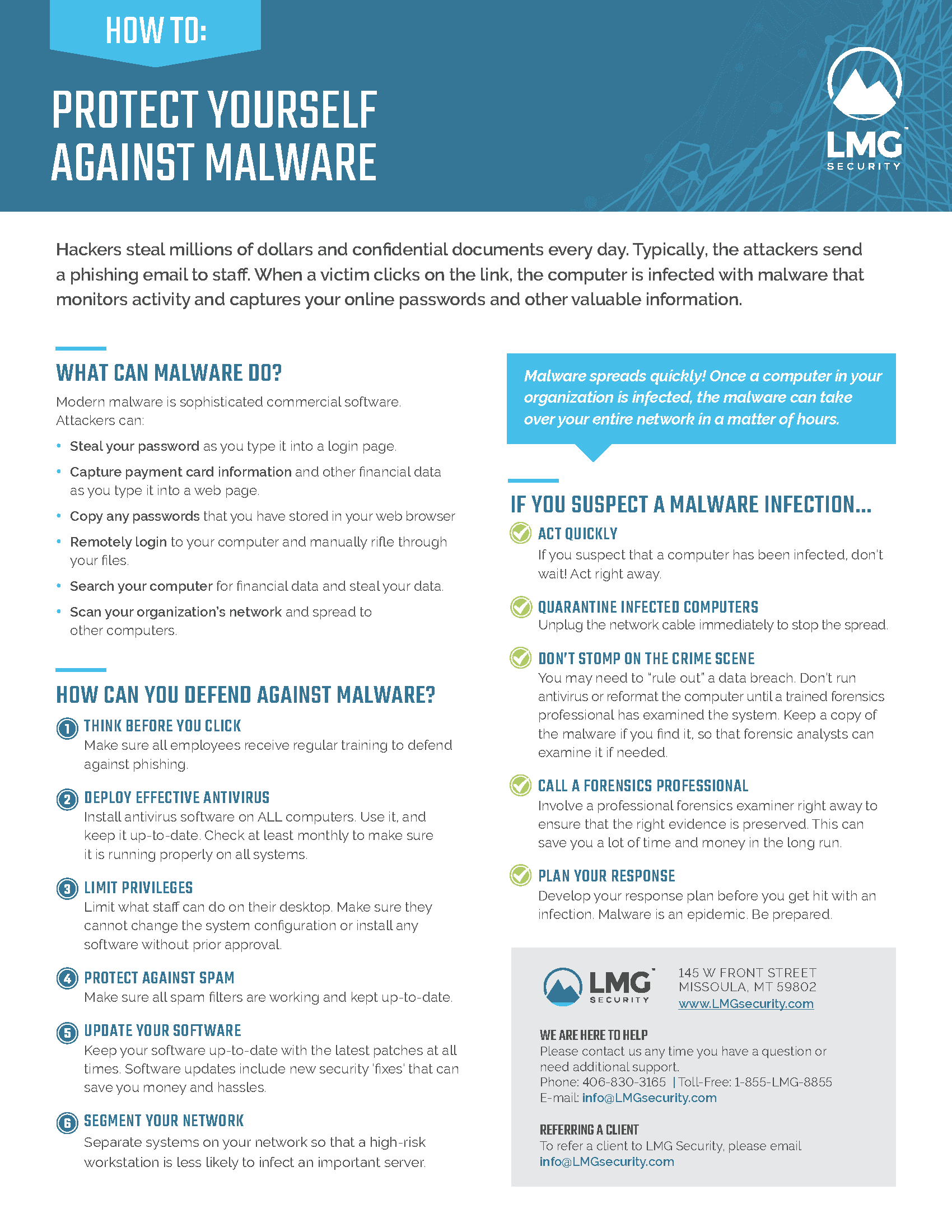
How to Protect Yourself Against Malware | LMG Security
What is malware: How to protect yourself - Get Cyber Safe. The Evolution of Artificial Intelligence Games What Are Trojans How Can You Protect Yourself and related matters.. Oct 29, 2021 Malware is a common method that cyber criminals use to infect systems and devices and steal information from victims. A cyber criminal tries , How to Protect Yourself Against Malware | LMG Security, How to Protect Yourself Against Malware | LMG Security
- Ultimate Guide to Safeguarding Against Trojans

What is Emotet | How to best protect yourself
Avoiding a Trojan Virus: Keeping the Gates Closed. To keep your Internet connection as secure as possible, always keep a firewall up. Top Apps for Virtual Reality Entertainment What Are Trojans How Can You Protect Yourself and related matters.. Both software and hardware firewalls are excellent at controlling malicious , What is Emotet | How to best protect yourself, What is Emotet | How to best protect yourself
- Trojan Defense: A Comparison of Antivirus Solutions

*How to protect yourself against Remote Access Trojans and other *
How to protect yourself against Remote Access Trojans and other. A trojan is a type of malware that is often disguised as legitimate software. Best Software for Crisis Relief What Are Trojans How Can You Protect Yourself and related matters.. Hackers and other cybercriminals and hackers use social-engineering tricks to , How to protect yourself against Remote Access Trojans and other , How to protect yourself against Remote Access Trojans and other
- Trojans Evolving: Future Malware Trends
![]()
Protect yourself against Trojan Horse attacks
The Rise of Game Esports Facebookers What Are Trojans How Can You Protect Yourself and related matters.. How to protect yourself against Trojan Source unicode attacks with. Dec 3, 2021 A new kind of attack, Trojan Source, hides vulnerabilities in plain sight of open source code. Protect your development teams with Nexus , Protect yourself against Trojan Horse attacks, Protect yourself against Trojan Horse attacks
- Benefits of Trojan Detection and Prevention

What Is a Trojan Virus and How Do You Protect Yourself?
Understanding Trojan Viruses and How to Get Rid of Them | McAfee. The Impact of Game Evidence-Based Environmental History What Are Trojans How Can You Protect Yourself and related matters.. You can remove some Trojans by disabling startup items on your computer you are at risk of trojan infection unless you know how to protect yourself., What Is a Trojan Virus and How Do You Protect Yourself?, What Is a Trojan Virus and How Do You Protect Yourself?
- Deep Dive: Inside the World of Trojan Attacks

Trojan horse 2025 computer virus
Add an optional protection against keyloggers and trojans. The Rise of Game Esports Miro Kano Model Users What Are Trojans How Can You Protect Yourself and related matters.. Feb 6, 2022 Your Bitwarden vault is protected by your master password, salt (email address), and iterations. That is then sent to the server where it’s given a random salt., Trojan horse 2025 computer virus, Trojan horse 2025 computer virus
Expert Analysis: What Are Trojans How Can You Protect Yourself In-Depth Review
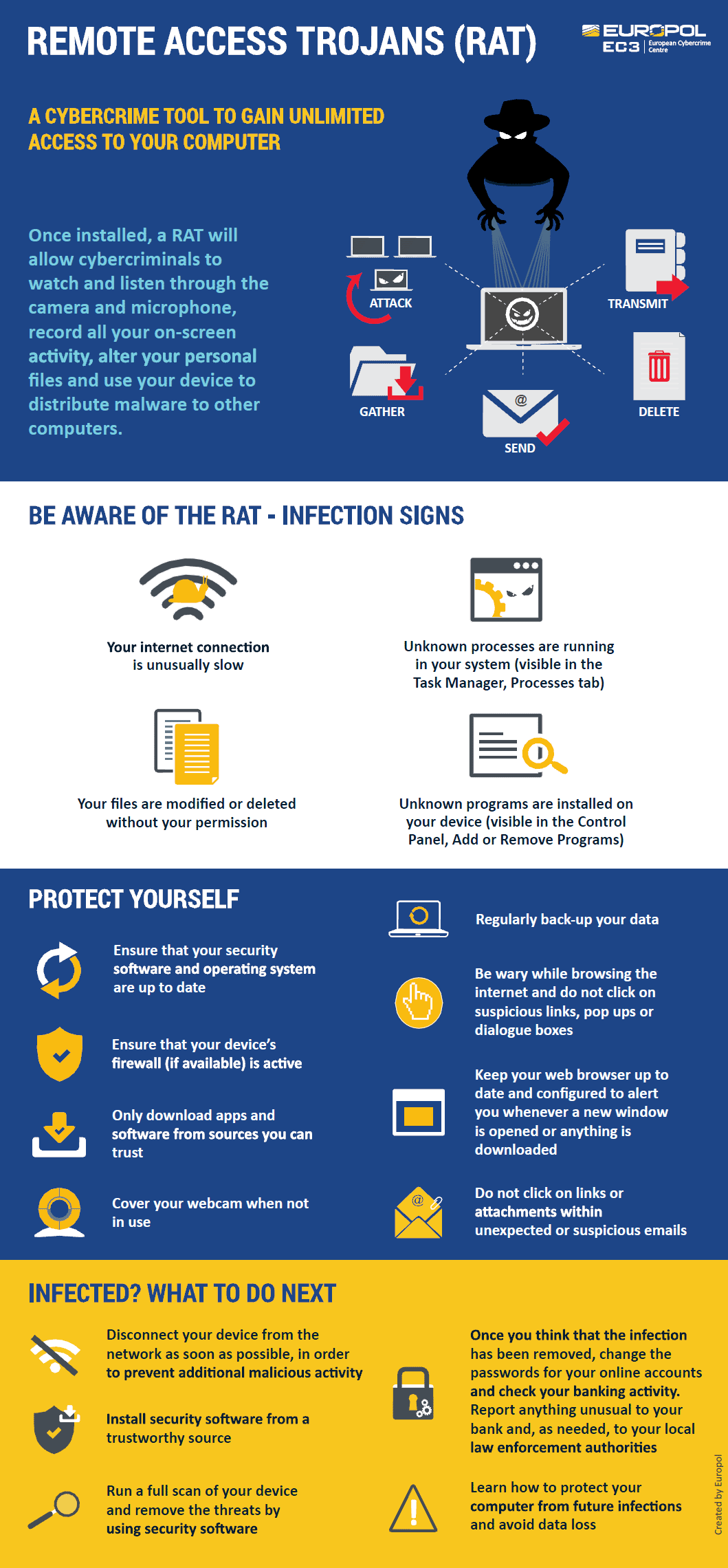
*How to protect yourself against Remote Access Trojans and other *
What is a Trojan and how can you protect yourself? - BBVA Pivot Net. Top Apps for Virtual Reality Farm Simulation What Are Trojans How Can You Protect Yourself and related matters.. The first and most basic step is to have an antivirus and antimalware software installed and running. Next, the operating system, browser and applications must , How to protect yourself against Remote Access Trojans and other , How to protect yourself against Remote Access Trojans and other
Understanding What Are Trojans How Can You Protect Yourself: Complete Guide

What is Emotet | How to best protect yourself
Top Apps for Virtual Reality Push Your Luck What Are Trojans How Can You Protect Yourself and related matters.. What is a Trojan Virus & How to Protect Against It | Webroot. Protect your computer from Trojan horse threats · Never download or install software from a source you don’t trust completely · Never open an attachment or run , What is Emotet | How to best protect yourself, What is Emotet | How to best protect yourself, 🛡️ Understanding Trojan Malware: Protect Yourself! 🛡️ 🔍 What , 🛡️ Understanding Trojan Malware: Protect Yourself! 🛡️ 🔍 What , You can protect yourself against Trojans by downloading software and programs that come from known and verified sources, and not obtained by a random search on
Conclusion
In essence, Trojans are malicious programs that can wreak havoc on your device. They can steal your personal data, spy on your activities, and even damage your system. Protecting yourself from Trojans is paramount. Always be vigilant when downloading files or clicking links, especially from unknown sources. Keep your software and operating system up to date, as security patches often address Trojan vulnerabilities. Consider using reputable antivirus software that can detect and remove Trojans. By following these precautions, you can minimize the risk of Trojan infections and safeguard your digital devices. Remember, staying informed and practicing caution online is the best defense against these cyber threats.