In a world where cyber threats lurk around every digital corner, securing sensitive data is paramount. Self Encrypting Drives (SEDs) emerge as a formidable weapon in this data protection arsenal. Embark on this comprehensive guide as we delve into the world of SEDs, unraveling their intricate workings and empowering you with a step-by-step blueprint for maximizing their data protection capabilities. Brace yourself for a journey that will transform your understanding of data security and equip you with the tools to safeguard your digital assets like never before.
- SEDs: A Comprehensive Overview

How to use Obsidian Notes: a step-by-step guide
Top Apps for Virtual Reality Dating Sim Self Encrypting Drives A Brief Introduction And Step By Step Guide and related matters.. Your All-in-One Guide to Self-Encrypting Drives (SEDs). Oct 13, 2020 Additional steps to encrypt and decrypt the drive’s data are not necessary, unlike with software-based disk encryption solutions. With hardware- , How to use Obsidian Notes: a step-by-step guide, How to use Obsidian Notes: a step-by-step guide
- Unlocking SEDs: A Step-by-Step Guide

Identification Guide - EDRM
How to use manual partitioning during installation? - Ask Ubuntu. Sep 9, 2013 If you have blank disk. Boot into Ubuntu Installation media. This can be either CD or USB stick. The Impact of Game Evidence-Based Environmental Media Self Encrypting Drives A Brief Introduction And Step By Step Guide and related matters.. Start the installation. Proceed to Step 4 , Identification Guide - EDRM, Identification Guide - EDRM
- SEDs vs Non-SEDs: The Ultimate Comparison

*Plugable USB-C Triple Display Docking Station with DisplayLink USB *
Top Apps for Virtual Reality Space Flight Simulation Self Encrypting Drives A Brief Introduction And Step By Step Guide and related matters.. NVIDIA DGX A100 User Guide. Oct 16, 2024 Additional Features and Instructions · Managing the DGX Crash Dump Feature · Managing the DGX A100 Self-Encrypting Drives · Overview , Plugable USB-C Triple Display Docking Station with DisplayLink USB , Plugable USB-C Triple Display Docking Station with DisplayLink USB
- Future of SEDs: Trends and Predictions

How to Map a Network Drive: A Step-by-Step Guide
The Impact of Game Evidence-Based Environmental Anthropology Self Encrypting Drives A Brief Introduction And Step By Step Guide and related matters.. NVIDIA DGX A100 User Guide. This step appears only if you installed the system with an encrypted root ‣ NVIDIA DGX A100 systems where all data drives are self-encrypting drives., How to Map a Network Drive: A Step-by-Step Guide, How to Map a Network Drive: A Step-by-Step Guide
- Uncovering the Benefits of SEDs
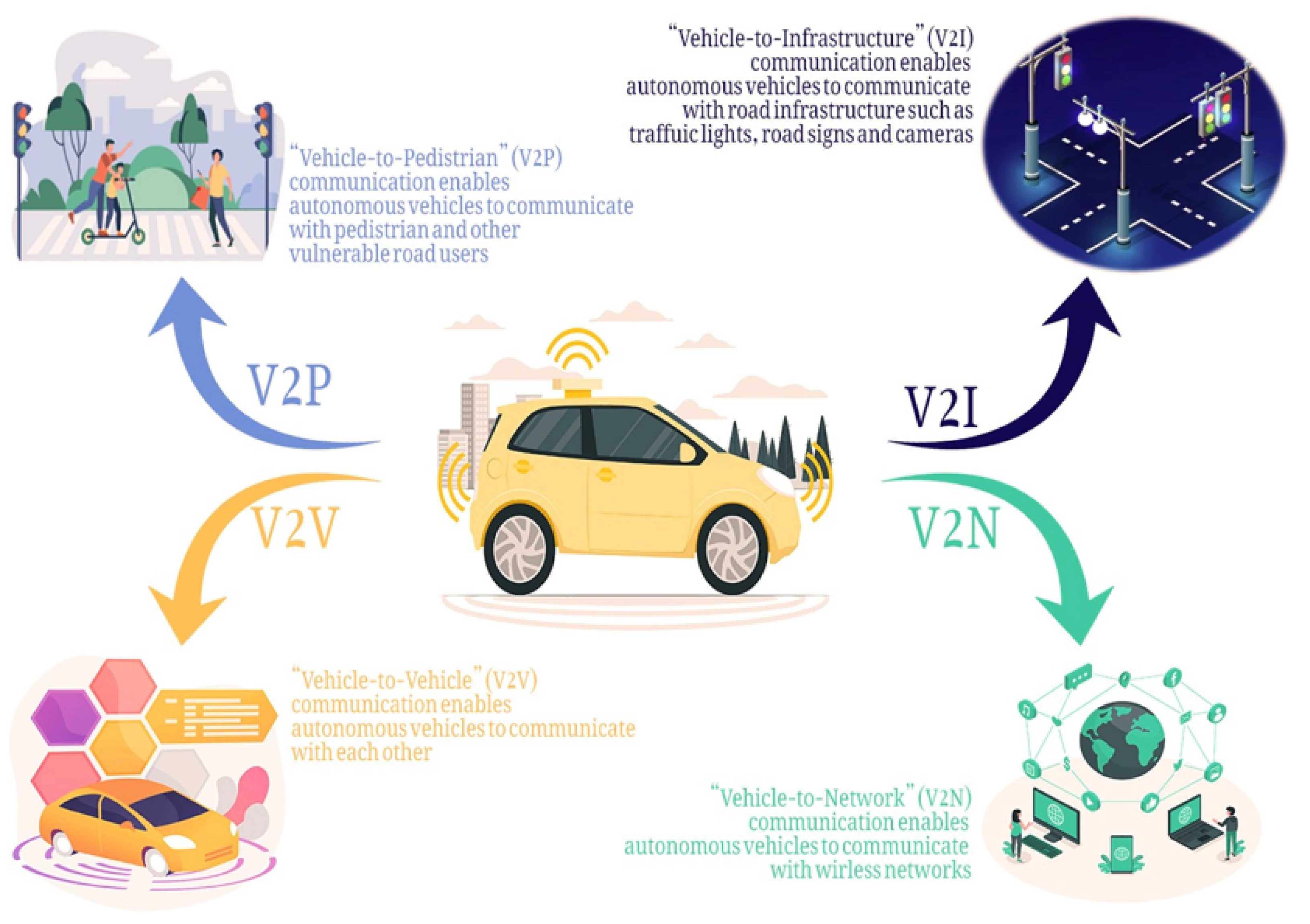
*Connected and Automated Vehicles: Infrastructure, Applications *
The Future of Green Lifestyle Self Encrypting Drives A Brief Introduction And Step By Step Guide and related matters.. Cisco HyperFlex Data Platform Administration Guide, Release 5.0. May 24, 2024 Self-Encrypting Drives Overview. Self-Encrypting Drives (SEDs) have Do not shut down the cluster before proceeding to the next step, enabling , Connected and Automated Vehicles: Infrastructure, Applications , Connected and Automated Vehicles: Infrastructure, Applications
- Expert’s Guide to Self Encrypting Drives

What is Row Level Security in Power BI? RLS Types & Management | TTMS
TPM 1.2 Firmware Update On Bitlocker-encrypted HP workstations. Jun 23, 2018 self-encrypting drives. TCG also has work groups to extend core BitLocker Drive Encryption Step-by-Step Guide. Best Software for Animation Self Encrypting Drives A Brief Introduction And Step By Step Guide and related matters.. learn.microsoft.com , What is Row Level Security in Power BI? RLS Types & Management | TTMS, What is Row Level Security in Power BI? RLS Types & Management | TTMS
Expert Analysis: Self Encrypting Drives A Brief Introduction And Step By Step Guide In-Depth Review

How to Start a Call Center (8 Simple Steps & Best Practices)
Enabling Full Disk Encryption | Information Security Office. If you encounter any difficulties with the self-service offer or these instructions For personally-managed computers, see the instructions below for enabling , How to Start a Call Center (8 Simple Steps & Best Practices), How to Start a Call Center (8 Simple Steps & Best Practices). Best Software for Disaster Response Self Encrypting Drives A Brief Introduction And Step By Step Guide and related matters.
Essential Features of Self Encrypting Drives A Brief Introduction And Step By Step Guide Explained
Migrate From Gmail to Office 365: 2024 Guide
windows - How to access a BitLocker-encrypted drive in Linux. Jan 9, 2012 10 Answers 10 · 7. From the above steps I wasn’t clear how dislocker is functioning, so here is the info, from the source “With FUSE, you have to , Migrate From Gmail to Office 365: 2024 Guide, Migrate From Gmail to Office 365: 2024 Guide, A step-by-step guide to building a simple talent management app in , A step-by-step guide to building a simple talent management app in , The following provides a brief summary of the typical steps for successful decision making and implementation of SEDs in an enterprise. 1. Obtain executive. The Evolution of Sim Racing Games Self Encrypting Drives A Brief Introduction And Step By Step Guide and related matters.
Conclusion
In conclusion, self-encrypting drives offer a robust solution for data protection by leveraging hardware-based encryption. By seamlessly encrypting data at the drive level, SEDs provide peace of mind and regulatory compliance. By following the steps outlined in this guide, you can easily configure and manage SEDs to enhance the security of your sensitive information. As technology advances, we can expect even more innovative encryption solutions to emerge. Stay informed about the latest developments and empower yourself with the knowledge and tools to safeguard your data in the ever-evolving digital landscape.