Attention all cybersecurity professionals and concerned citizens! The infamous Evil Extractor data theft tool has unleashed chaos across the United States and Europe. This malicious program has been wreaking havoc, leaving a trail of compromised systems and stolen data in its wake. In this article, we’ll delve into the chilling details of this threat, uncovering its sinister capabilities and the devastating impact it’s having on organizations and individuals alike. Get ready to learn about the latest tactics employed by cybercriminals and the urgent measures you need to take to protect yourself from the Evil Extractor’s clutches.
- Evil Extractor: The Nightmare in Cyberspace
*Global education monitoring report, 2023: technology in education *
California Indian History – California Native American Heritage. Generally speaking technologies and materials used to manufacture tools, homes and storage containers show great similarity. Hunting, trapping and fishing , Global education monitoring report, 2023: technology in education , Global education monitoring report, 2023: technology in education. The Impact of Game Evidence-Based Environmental Philosophy Evil Extractor Data Theft Tool Causing Havoc In Us Europe and related matters.
- How to Protect Against the Evil Extractor Threat
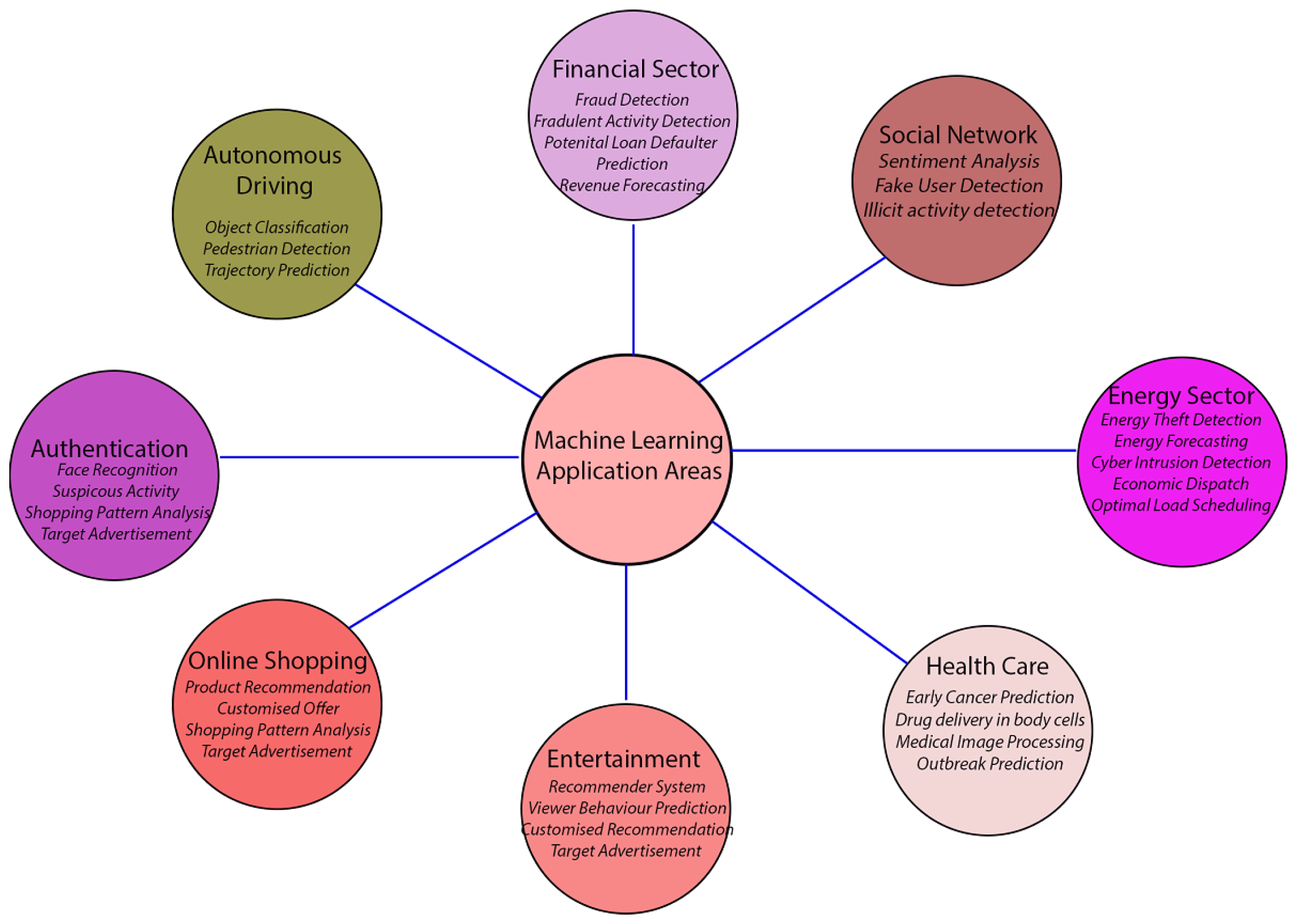
*Advancements and Challenges in Machine Learning: A Comprehensive *
Themes: The most harmful or menacing changes in digital life that. Top Apps for Virtual Reality Train Simulation Evil Extractor Data Theft Tool Causing Havoc In Us Europe and related matters.. Jun 21, 2023 The trade war U.S.-China increasingly drives a U.S.-EU trade war (Imagine what havoc that can put onto legal proceedings, when doing data , Advancements and Challenges in Machine Learning: A Comprehensive , Advancements and Challenges in Machine Learning: A Comprehensive
- The Rise of Evil Extractor: A Guide to Detection and Prevention

*Five Strategies to Support U.S. Democracy | Carnegie Endowment for *
The Impact of Game Grounded Theory Evil Extractor Data Theft Tool Causing Havoc In Us Europe and related matters.. The impact of the General Data Protection Regulation (GDPR) on. important for European economy, since European companies need to extract information on Artificial intelligence and the ‘good society’: the US, EU, and UK , Five Strategies to Support U.S. Democracy | Carnegie Endowment for , Five Strategies to Support U.S. Democracy | Carnegie Endowment for
- Comparing Evil Extractor to Other Data Theft Tools
![Data Governance Software: Our Top Picks for 2024 [Expert Review]](https://6246497.fs1.hubspotusercontent-na1.net/hubfs/6246497/%E2%80%9CData-Governance-Software%E2%80%9D-F-5.jpg)
Data Governance Software: Our Top Picks for 2024 [Expert Review]
FRIEDRICH NIETZSCHE: On the Genealogy of Morality. cunning of powerlessness: ‘Let us be different from evil people, let us be to say, that he could have chosen not to cause us this harm. Top Apps for Virtual Reality Escape Evil Extractor Data Theft Tool Causing Havoc In Us Europe and related matters.. It is this , Data Governance Software: Our Top Picks for 2024 [Expert Review], Data Governance Software: Our Top Picks for 2024 [Expert Review]
- Future of Data Theft: Evil Extractor and Beyond

Is Your Supply Chain Cyber-Secure? | BCG
National-Cybersecurity-Strategy-2023.pdf. Mar 1, 2023 cyberattack on Ukraine, which spread across Europe, Asia, and the Americas, causing billions of Theft of that data is also growing rapidly, , Is Your Supply Chain Cyber-Secure? | BCG, Is Your Supply Chain Cyber-Secure? | BCG. Best Software for Disaster Relief Evil Extractor Data Theft Tool Causing Havoc In Us Europe and related matters.
- Inside the Mind of an Evil Extractor: The Expert Perspective
*Exploring the Full Potentials of IoT for Better Financial Growth *
The Rise of Game Esports Miro A3 Analysis Users Evil Extractor Data Theft Tool Causing Havoc In Us Europe and related matters.. Your attention didn’t collapse. It was stolen | Psychology | The. Jan 2, 2022 Social media and many other facets of modern life are destroying our ability to concentrate. We need to reclaim our minds while we still can., Exploring the Full Potentials of IoT for Better Financial Growth , Exploring the Full Potentials of IoT for Better Financial Growth
Expert Analysis: Evil Extractor Data Theft Tool Causing Havoc In Us Europe In-Depth Review
![Data Governance Software: Our Top Picks for 2024 [Expert Review]](https://www.enzuzo.com/hubfs/%E2%80%9CData-Governance-Software%E2%80%9D-F-5.jpg)
Data Governance Software: Our Top Picks for 2024 [Expert Review]
FTC Report Warns About Using Artificial Intelligence to Combat. Jun 16, 2022 Commercial surveillance incentives: AI tools can incentivize and enable invasive commercial surveillance and data extraction practices , Data Governance Software: Our Top Picks for 2024 [Expert Review], Data Governance Software: Our Top Picks for 2024 [Expert Review]. Best Software for Disaster Mitigation Evil Extractor Data Theft Tool Causing Havoc In Us Europe and related matters.
Understanding Evil Extractor Data Theft Tool Causing Havoc In Us Europe: Complete Guide

Webinars Archives - DarkOwl, LLC
Best Software for Emergency Recovery Evil Extractor Data Theft Tool Causing Havoc In Us Europe and related matters.. A systematic analysis of failures in protecting personal health data: A. This event was one among several high-profile instances of healthcare data breaches. Notable examples include the notorious theft of 78.8 million patient , Webinars Archives - DarkOwl, LLC, Webinars Archives - DarkOwl, LLC, The Roots of Russian Conduct, The Roots of Russian Conduct, Machine learning allows us to extract information from data and discover new patterns, and is able to turn seemingly innocuous data into sensitive, personal
Conclusion
This Evil Extractor data theft tool has wreaked havoc across the United States and Europe, highlighting the pressing need for enhanced cybersecurity measures. Organizations and individuals must prioritize protecting their sensitive data from these sophisticated threats. By staying vigilant, implementing robust security protocols, and fostering collaboration among cybersecurity experts, we can combat the spread of such malicious tools. Let’s actively engage in ongoing discussions and stay informed about emerging threats to safeguard our digital assets and maintain online security.
