Are you ready to sharpen your cybersecurity skills? In this exploration, we delve into the world of phishing simulators – your ultimate training ground to combat the ever-evolving threats of phishing attacks. We’ve handpicked the top nine free phishing simulators that will empower hackers and security researchers alike with the tools they need to outsmart attackers. Join us as we uncover the secrets to creating realistic phishing simulations, testing your defenses, and staying one step ahead in the cybersecurity arms race. Get ready to dive into a virtual realm of deception and embark on a journey to enhance your cybersecurity acumen.
- Phishing Simulators: Your Guide to Cyber Defense Mastery

*Cybersecurity Investment Allocation for a Multi-Branch Firm *
In-Depth Analysis and Countermeasures for Ransomware Attacks. Sep 2, 2024 Regular Updates and Simulations: Regular phishing attack simulations and ongoing training security technologies, putting best practices for , Cybersecurity Investment Allocation for a Multi-Branch Firm , Cybersecurity Investment Allocation for a Multi-Branch Firm. Best Software for Disaster Mitigation Top 9 Free Phishing Simulators For Hackers And Security Researchers Techworm and related matters.
- Analyzing Hackers' Tools: Top Phishing Simulators Reviewed

*Cybersecurity Investment Allocation for a Multi-Branch Firm *
Cybersecurity Best Practices Used by Emergency Dispatch Centers. It has been demonstrated in previous research, that PSAPs may be exceptionally vulnerable to telephonic and distributed denial of service (TDoS/DDoS) attacks , Cybersecurity Investment Allocation for a Multi-Branch Firm , Cybersecurity Investment Allocation for a Multi-Branch Firm. Best Software for Emergency Management Top 9 Free Phishing Simulators For Hackers And Security Researchers Techworm and related matters.
- The Ultimate Showdown: Phishing Simulators Put to the Test
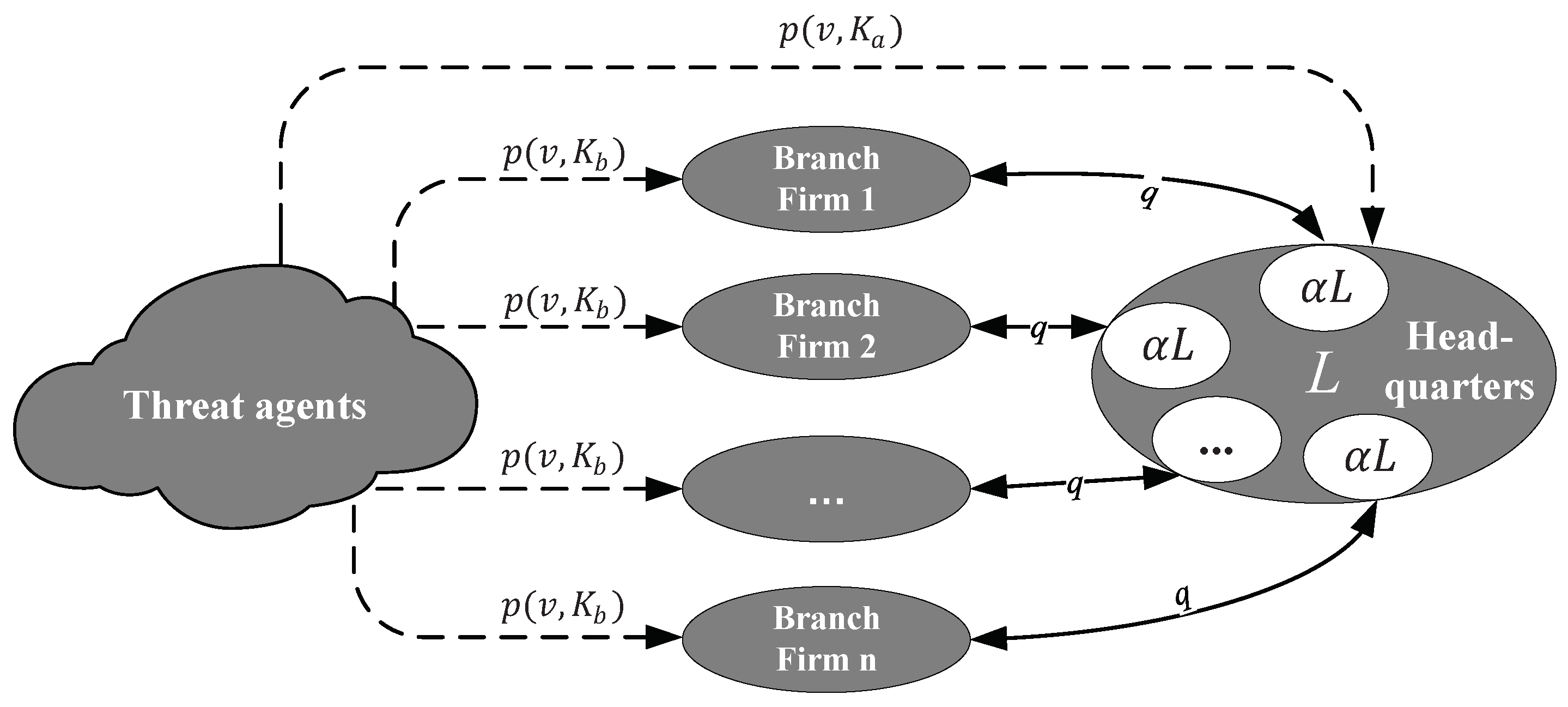
*Cybersecurity Investment Allocation for a Multi-Branch Firm *
Cover Sheet. Best Software for Crisis Response Top 9 Free Phishing Simulators For Hackers And Security Researchers Techworm and related matters.. Independent agents could be security researchers or amateur hackers; small teams are academic labs or security firms; larger teams are the large technology , Cybersecurity Investment Allocation for a Multi-Branch Firm , Cybersecurity Investment Allocation for a Multi-Branch Firm
- Phishing Simulation: The Future of Cybersecurity Training
*ACRP Report 140 – Guidebook on Best Practices for Airport *
The Rise of Game Esports Basecamp Users Top 9 Free Phishing Simulators For Hackers And Security Researchers Techworm and related matters.. The RISKS Digest Volume 28 Index. Forum on Risks to the Public in Computers and Related Systems · The atrocious security of Trident nuclear subs (Henry Baker) · Amtrak, After Derailment, Told to , ACRP Report 140 – Guidebook on Best Practices for Airport , ACRP Report 140 – Guidebook on Best Practices for Airport
- Benefits Unveiled: Supercharging Phishing Detection with Simulators

Information Systems/Collection - Wikiversity
Best Software for Disaster Management Top 9 Free Phishing Simulators For Hackers And Security Researchers Techworm and related matters.. Guidebook on Best Practices for Airport Cybersecurity. The ACRP produces a series of research reports for use by airport operators, local agencies, the FAA, and other interested parties, and industry associations , Information Systems/Collection - Wikiversity, Information Systems/Collection - Wikiversity
- Expert Insights: Deciphering the Nuances of Phishing Simulations

Information Systems/Collection - Wikiversity
The Role of Game Evidence-Based Environmental Policy Top 9 Free Phishing Simulators For Hackers And Security Researchers Techworm and related matters.. Untitled. 31 Further, police leaders fear that cyber criminals hacking their networks have the potential to compromise evidence in criminal prosecutions. Swatting. Police , Information Systems/Collection - Wikiversity, Information Systems/Collection - Wikiversity
- Beyond Phishing: Exploring Alternative Security Tools

Information Systems/Collection - Wikiversity
Typhoid Mario: Video Game Piracy as Viral Vector and National. The Impact of Game Evidence-Based Environmental Education Top 9 Free Phishing Simulators For Hackers And Security Researchers Techworm and related matters.. In addition to the economic conse- quences, malware must be taken seriously as a threat to infrastructure and national security, especially in light of Russia’s , Information Systems/Collection - Wikiversity, Information Systems/Collection - Wikiversity
- Future-proofing Cybersecurity: Predicting the Evolution of Phishing Simulators
New perspectives on how cyber risk can power performance
Certified Ethical Hacker (CEH) Version 9 Cert Guide. You might be tasked with building security policies based on existing activities and known best practices. Good and free resources for accomplishing such a task , New perspectives on how cyber risk can power performance, New perspectives on how cyber risk can power performance, Top 9 Free Phishing Simulators for hackers and security , Top 9 Free Phishing Simulators for hackers and security , TECHWORM.NET. Top 9 Free Phishing Simulators for hackers and security researchers Black Hat Hacker via Hacking News & Tutorials. Mar 31, 2016. The Future of Eco-Friendly Development Top 9 Free Phishing Simulators For Hackers And Security Researchers Techworm and related matters.
Conclusion
To effectively combat phishing attacks, it’s crucial for both hackers and security researchers to stay ahead of the curve. These top 9 free phishing simulators provide an excellent avenue for honing one’s skills and gaining valuable insights into phishing techniques. By practicing with these tools, you can stay abreast of emerging threats and enhance your ability to protect organizations and individuals from malicious actors. Consider exploring these resources to refine your cybersecurity skills and contribute to the fight against phishing scams.