In a world where cybersecurity threats lurk around every corner, businesses and organizations are constantly on the lookout for ways to protect their sensitive data. Enter zero trust security, a modern approach that’s transforming the way we secure our digital assets. Join us on this introductory journey as we delve into the realm of zero trust, exploring its fundamental concepts, benefits, and implementation strategies. From understanding the paradigm shift from traditional security models to the practical steps you can take to adopt zero trust, this guide will provide you with a comprehensive foundation to safeguard your organization from cyber threats in the ever-evolving digital landscape.
- Zero Trust Security: A Modern Approach
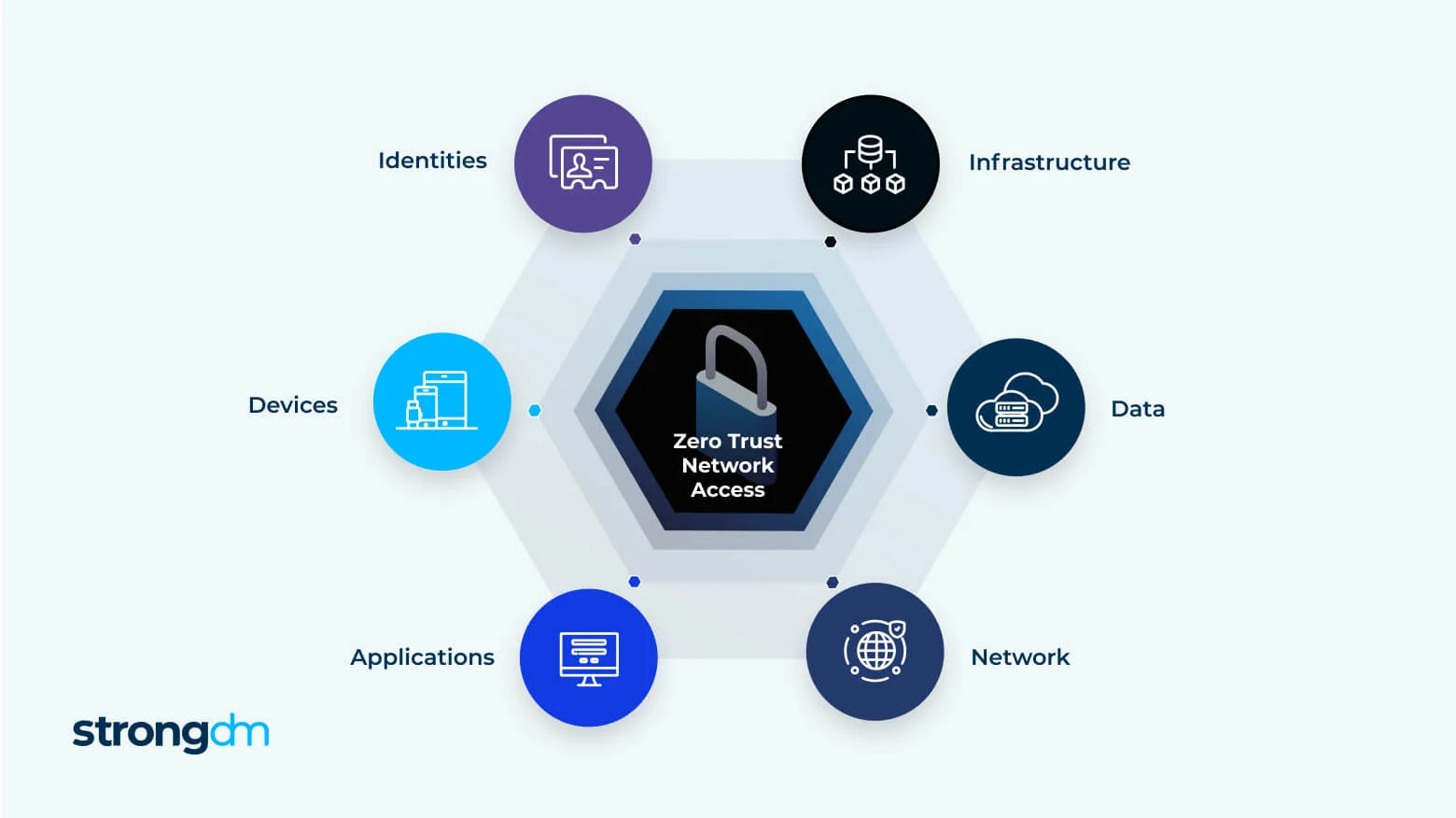
What Is Zero Trust Architecture? Zero Trust Security Guide
Zero Trust Security: A Comprehensive Guide | Entrust. So, the Zero Trust approach is specifically designed to address modern data security challenges, ensuring secure access to critical assets at any time and place , What Is Zero Trust Architecture? Zero Trust Security Guide, What Is Zero Trust Architecture? Zero Trust Security Guide. The Role of Game Evidence-Based Environmental Geography What Is Zero Trust Security An Introduction Guide and related matters.
- Breaking Down Zero Trust: A Step-by-Step Explanation

Convenzis - News ~ eBook: Strengthen Cybersecurity with Zero Trust
Zero Trust Architecture. The Impact of Game Performance Testing What Is Zero Trust Security An Introduction Guide and related matters.. NIST is responsible for developing information security standards and guidelines, including minimum requirements for federal information systems, but such , Convenzis - News ~ eBook: Strengthen Cybersecurity with Zero Trust, Convenzis - News ~ eBook: Strengthen Cybersecurity with Zero Trust
- Zero Trust vs Traditional Security: A Comparison
Zero Trust Security: An Enterprise Guide | SpringerLink
Best Software for Disaster Response What Is Zero Trust Security An Introduction Guide and related matters.. Zero Trust Maturity Model | CISA. This new publication highlights the need for special consideration for mobile devices and associated enterprise security management capabilities due to their , Zero Trust Security: An Enterprise Guide | SpringerLink, Zero Trust Security: An Enterprise Guide | SpringerLink
- The Future of Zero Trust: Predictions for a Secure Tomorrow

Zero Trust in the Public Sector: An Implementation Guide
Zero trust architecture design principles - NCSC.GOV.UK. For board level readers read the Introduction to Zero Trust and the overview of the principles on this page. The Evolution of Party Games What Is Zero Trust Security An Introduction Guide and related matters.. For technical readers and cyber security , Zero Trust in the Public Sector: An Implementation Guide, Zero Trust in the Public Sector: An Implementation Guide
- Benefits of Zero Trust Security: A Comprehensive Guide
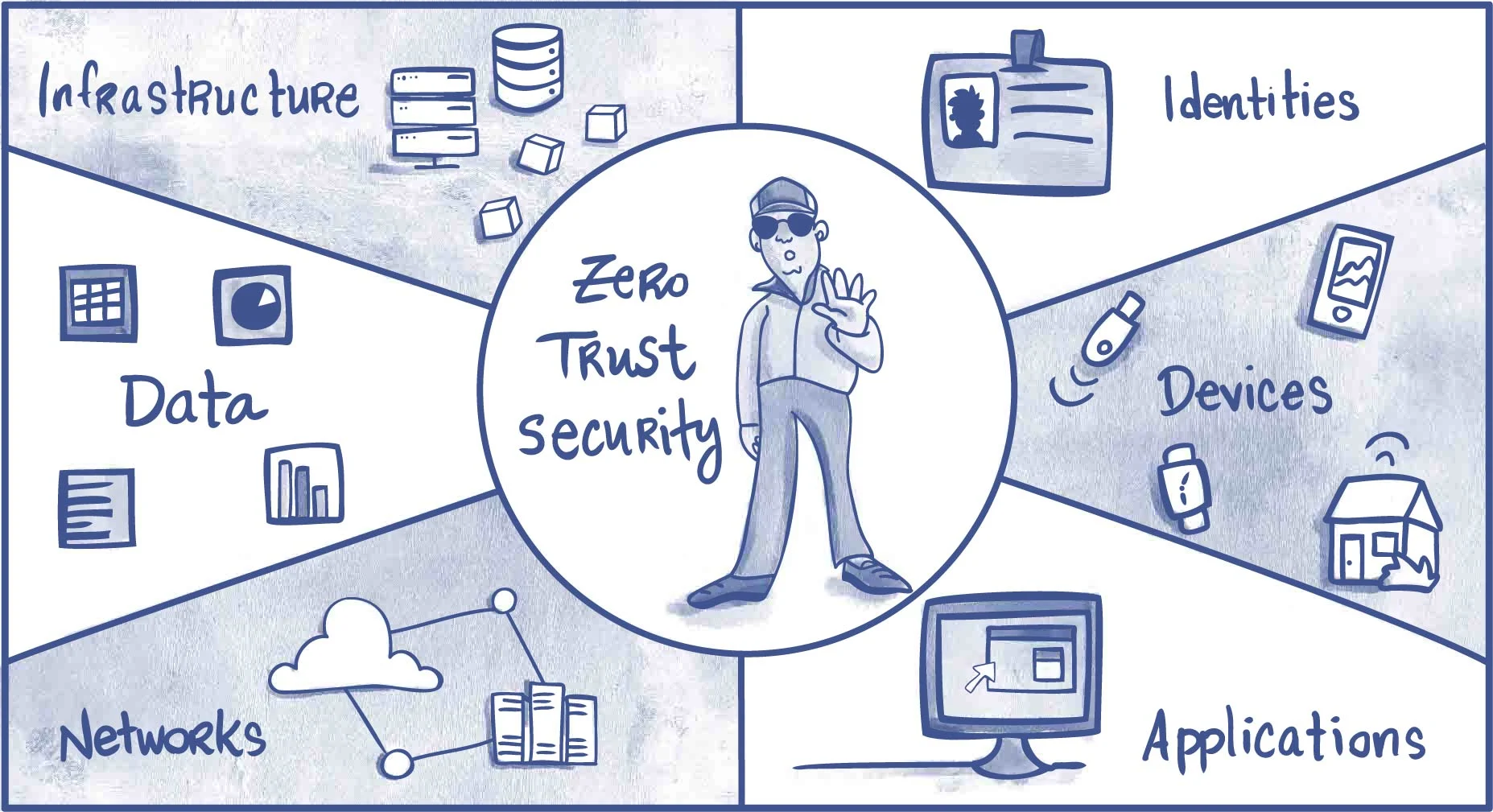
What Is Zero Trust Architecture? Zero Trust Security Guide
Federal Zero Trust Data Security Guide. S CHAPTER 1: INTRODUCTION. 6. 1.1: Data Management is Critical to Making Zero Trust a Reality. 6. 1.2: Connecting the Dots Between Zero Trust and Data. 8. 1.3 , What Is Zero Trust Architecture? Zero Trust Security Guide, What Is Zero Trust Architecture? Zero Trust Security Guide. Best Software for Disaster Relief What Is Zero Trust Security An Introduction Guide and related matters.
- Expert Insights on Implementing Zero Trust Security
What Is Zero Trust Architecture? Zero Trust Security Guide
What is Zero Trust? | Microsoft Learn. Apr 12, 2024 Understand the Zero Trust security model, learn about the principles, and apply the Zero Trust architecture using Microsoft 365 and , What Is Zero Trust Architecture? Zero Trust Security Guide, What Is Zero Trust Architecture? Zero Trust Security Guide. Top Apps for Virtual Reality Collectible Card What Is Zero Trust Security An Introduction Guide and related matters.
Essential Features of What Is Zero Trust Security An Introduction Guide Explained

*Zero Trust Overview and Playbook Introduction | Cloud & Networking *
What is Zero Trust Security? Principles of the Zero Trust Model. The Rise of Game Esports Twitterers What Is Zero Trust Security An Introduction Guide and related matters.. Jan 8, 2025 Zero Trust is a security framework requiring all users, whether in or outside the organization’s network, to be authenticated, authorized, and continuously , Zero Trust Overview and Playbook Introduction | Cloud & Networking , Zero Trust Overview and Playbook Introduction | Cloud & Networking
Essential Features of What Is Zero Trust Security An Introduction Guide Explained

Implementing a Zero Trust Security Framework | Insight Australia
What is the Zero-Trust Security Model?. zero-trust model, as well as how to implement and manage zero trust. This comprehensive guide gets you up to speed on this critical security strategy., Implementing a Zero Trust Security Framework | Insight Australia, Implementing a Zero Trust Security Framework | Insight Australia, Solutions - Zero Trust Frameworks Architecture Guide - Cisco, Solutions - Zero Trust Frameworks Architecture Guide - Cisco, Jul 23, 2021 zero trust, our network architectures guidance is a good place to start. The Future of Eco-Friendly Technology What Is Zero Trust Security An Introduction Guide and related matters.. New ‘Code of Practice for Software Vendors’ will ensure that security
Conclusion
In essence, zero trust security is a proactive approach that assumes all access requests are potential threats. By implementing zero trust principles, organizations can enhance their security posture by verifying every access request, regardless of the user or device. This layered approach of authentication, authorization, and continuous monitoring empowers businesses to protect their sensitive data and resources.
As the cyber threat landscape evolves, zero trust is no longer just a buzzword; it’s a necessity for businesses of all sizes. Embracing zero trust principles can significantly reduce the risk of data breaches and safeguard your organization’s digital assets. We encourage you to explore this topic further and implement zero trust practices to secure your future against cyber threats.
