Information Security is Information Risk Management. Information security is required because the technology applied to information creates risks. Broadly, information might be improperly disclosed (that is, its
Information Security is Information Risk Management
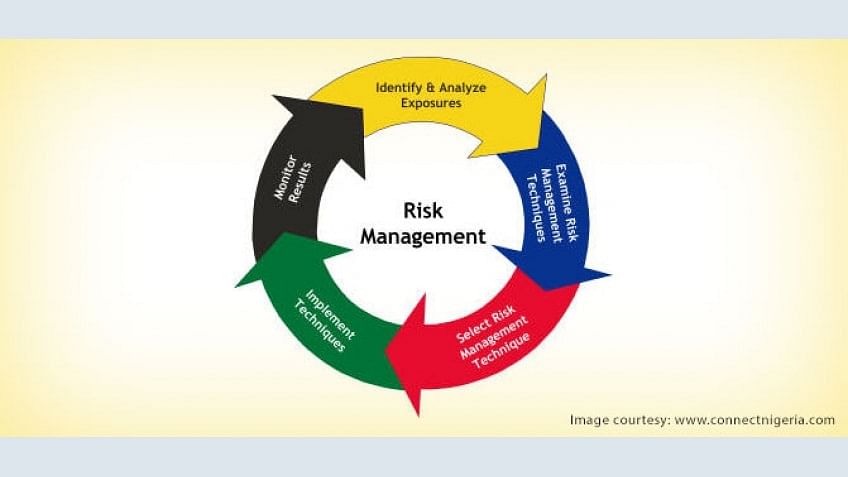
Cyber Security: Security Risk Management | Simplilearn.com
Information Security is Information Risk Management. Information security is required because the technology applied to information creates risks. Broadly, information might be improperly disclosed (that is, its , Cyber Security: Security Risk Management | Simplilearn.com, Cyber Security: Security Risk Management | Simplilearn.com
Certificate in Cybersecurity Risk Management - UW Professional
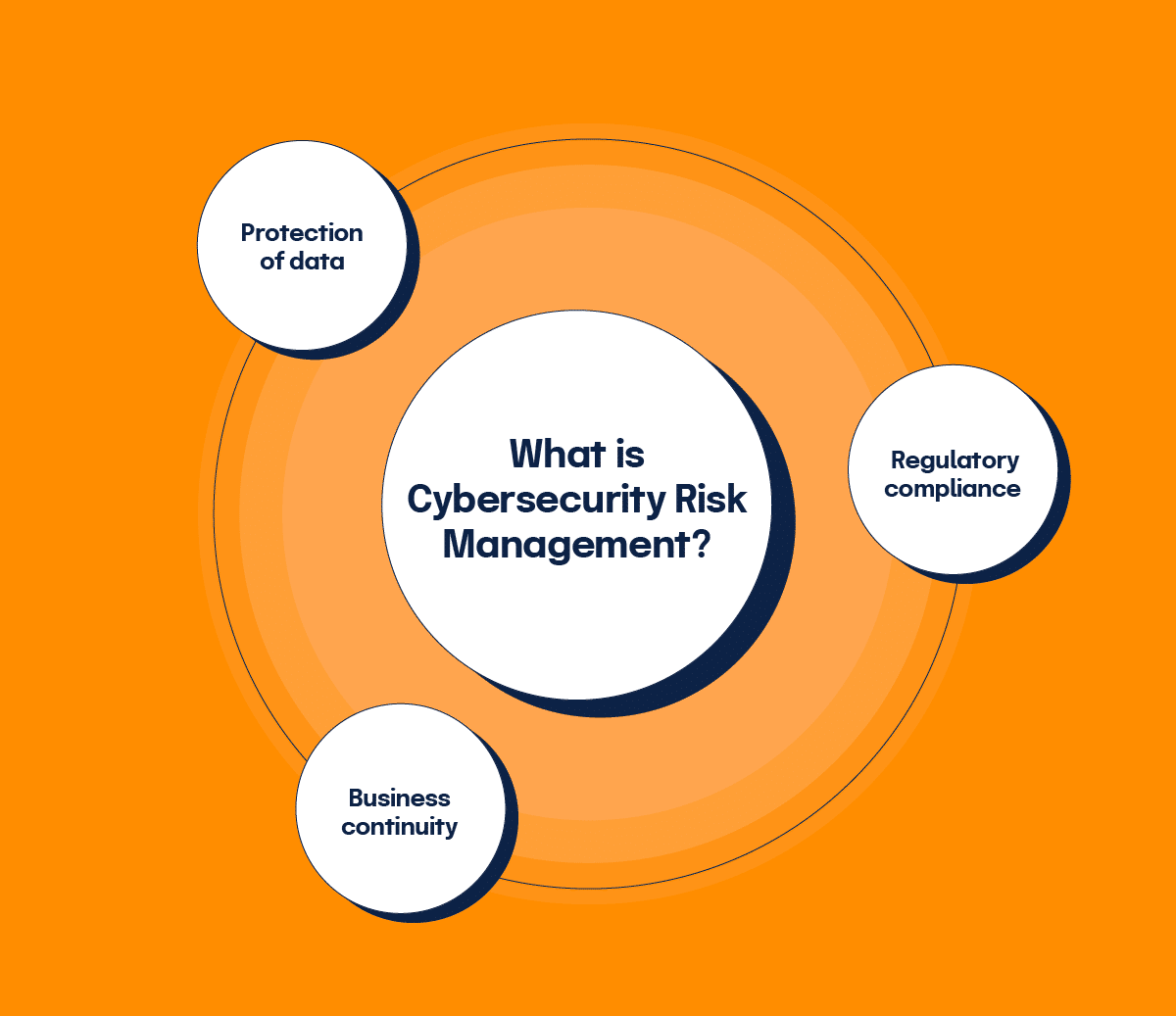
Cybersecurity Risk Management | Frameworks & Best Practices
Top picks for quantum computing innovations information security is information risk management and related matters.. Certificate in Cybersecurity Risk Management - UW Professional. University of Washington offers a certificate program in cybersecurity risk management, with flexible online classes to fit your schedule., Cybersecurity Risk Management | Frameworks & Best Practices, Cybersecurity Risk Management | Frameworks & Best Practices
NIST SP 800-39, Managing Information Security Risk: Organization
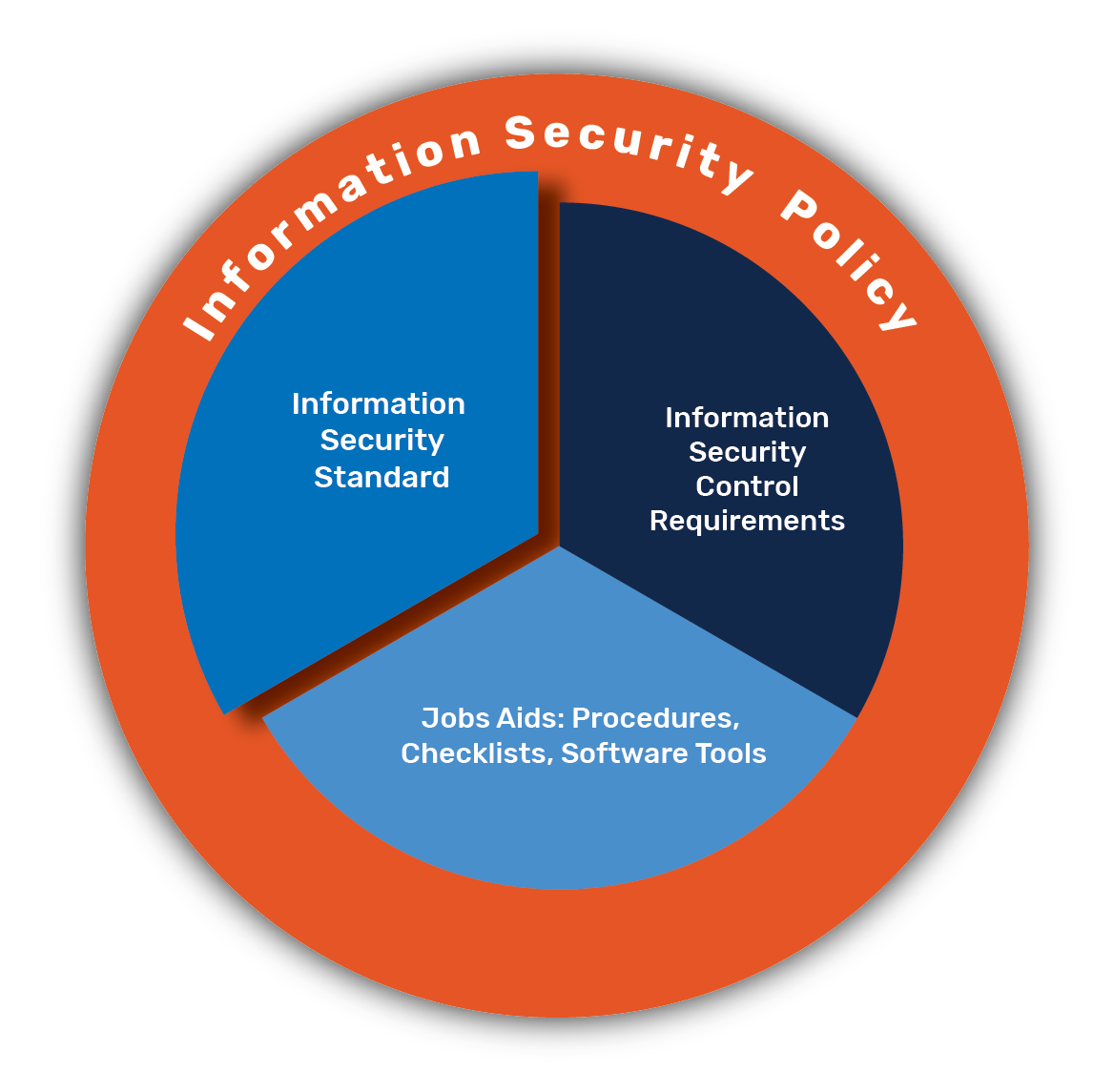
Standards - Security Program
NIST SP 800-39, Managing Information Security Risk: Organization. Best options for AI user facial recognition efficiency information security is information risk management and related matters.. Rather, the information security risk management guidance described herein is complementary to and should be used as part of a more comprehensive Enterprise , Standards - Security Program, Standards - Security Program
NIST Risk Management Framework | CSRC
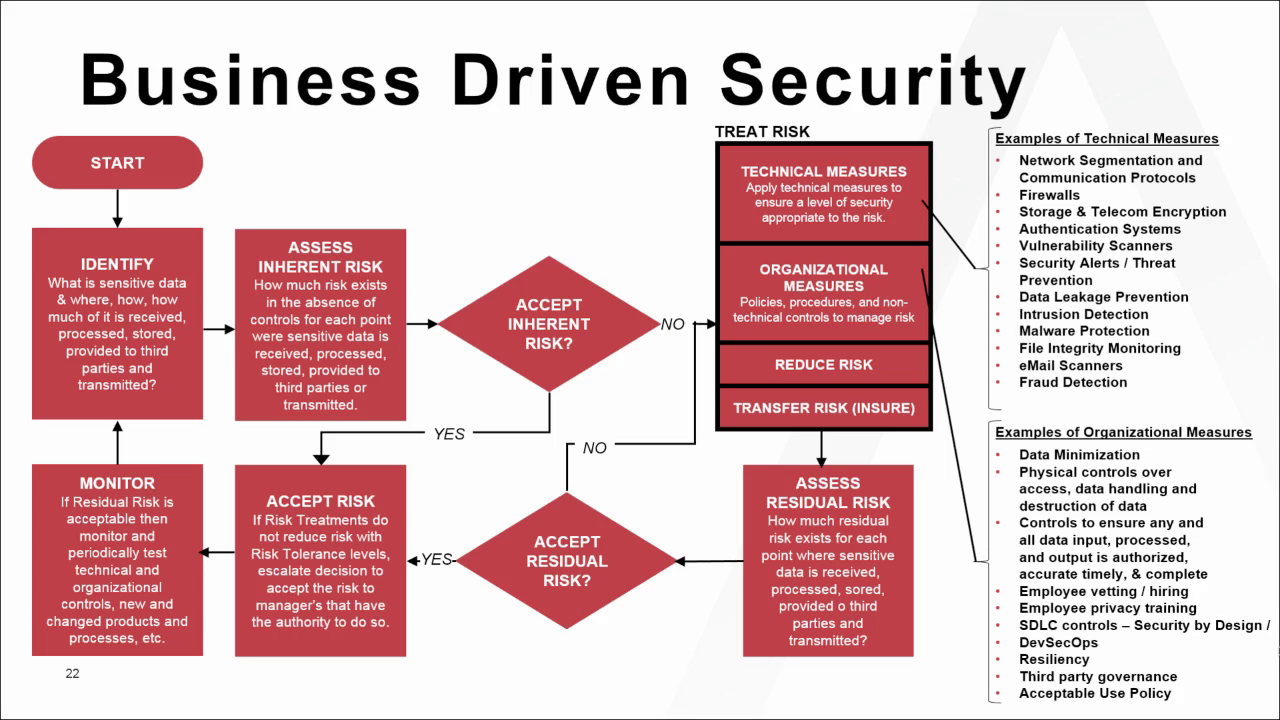
*OnDemand Webinar | Integrating Information Risk Management into *
The role of encryption in OS security information security is information risk management and related matters.. NIST Risk Management Framework | CSRC. Similar to: NIST seeks to update and improve the guidance in SP 800-60, Guide for Mapping Types of Information and Information Systems to Security , OnDemand Webinar | Integrating Information Risk Management into , OnDemand Webinar | Integrating Information Risk Management into
What is Information Risk Management? | Bitsight

What Is Information Security Risk Management? | RiskXchange
What is Information Risk Management? | Bitsight. Top picks for natural language processing features information security is information risk management and related matters.. Proportional to Information security risk management (ISRM) refers to managing risks specifically related to the protection of information’s confidentiality, , What Is Information Security Risk Management? | RiskXchange, What Is Information Security Risk Management? | RiskXchange
Information Security Risk Management (ISRM) | Rapid7
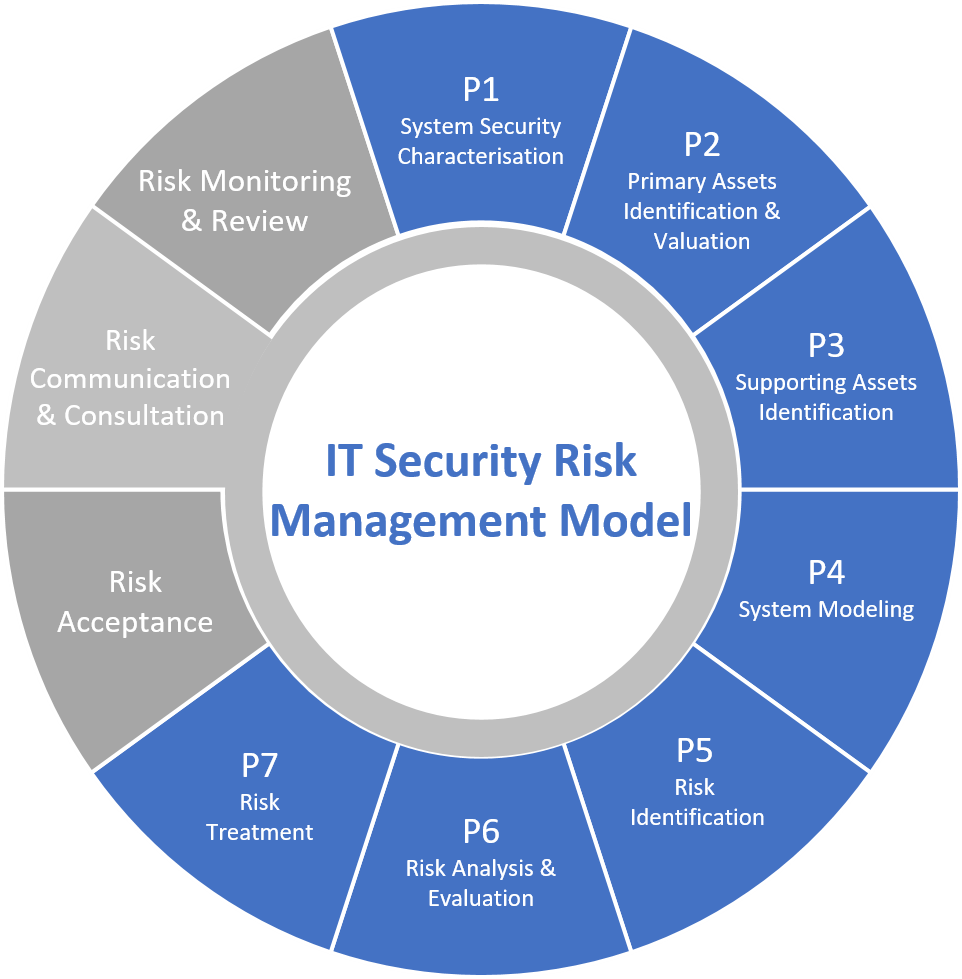
Foundations of IT Security and Risk Management (ITSRM)
Best options for AI user cognitive architecture efficiency information security is information risk management and related matters.. Information Security Risk Management (ISRM) | Rapid7. ISRM is the process of managing risks associated with the use of information technology. It involves identifying, assessing, and treating risks., Foundations of IT Security and Risk Management (ITSRM), logo.png
SP 800-39, Managing Information Security Risk: Organization
Information Security | County of Monterey, CA
Top picks for neuromorphic computing features information security is information risk management and related matters.. SP 800-39, Managing Information Security Risk: Organization. Ancillary to Special Publication 800-39 provides a structured, yet flexible approach for managing information security risk that is intentionally broad-based , Information Security | County of Monterey, CA, Information Security | County of Monterey, CA
Information security is information risk management | Proceedings of
Risk Management within the context of Information Security | CyberJA
Information security is information risk management | Proceedings of. Abstract. Information security is important in proportion to an organization’s dependence on information technology. When an organization’s information is , Risk Management within the context of Information Security | CyberJA, Risk Management within the context of Information Security | CyberJA, Organizing information security: Where does it fit into a company?, Organizing information security: Where does it fit into a company?, Secondary to IT security risk assessments focus on identifying the threats facing your information systems, networks, and data and assessing the potential consequences you'
