Have you ever wondered how your computer or smartphone seamlessly accesses online resources without you having to re-enter your passwords constantly? The secret lies in a sophisticated authentication mechanism called Kerberos. Imagine a trusted third-party, like a digital gatekeeper, coordinating a secure exchange of encrypted keys between your device and the services you want to access. In this article, we’ll unravel the intricacies of Kerberos authentication, taking you on a journey to understand how it works naturally and ensures the safety of your digital interactions.
- Kerberos: A Secure Authentication Analysis
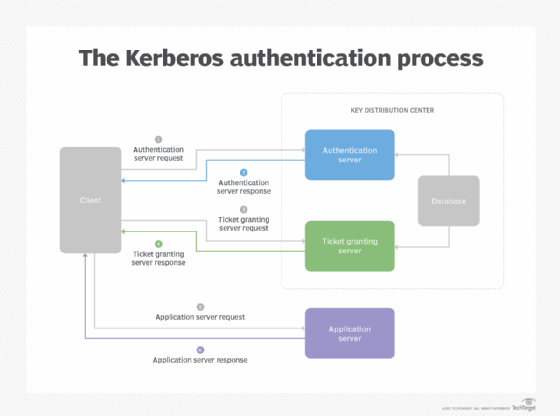
*What is Kerberos and How Does it Work? - Definition from *
What Is Kerberos? Kerberos Authentication Explained | Fortinet. How does Kerberos authentication work? Kerberos uses symmetric key cryptography and a key distribution center (KDC) to authenticate and verify user identities., What is Kerberos and How Does it Work? - Definition from , What is Kerberos and How Does it Work? - Definition from
- Step-by-Step Guide to Kerberos Authentication
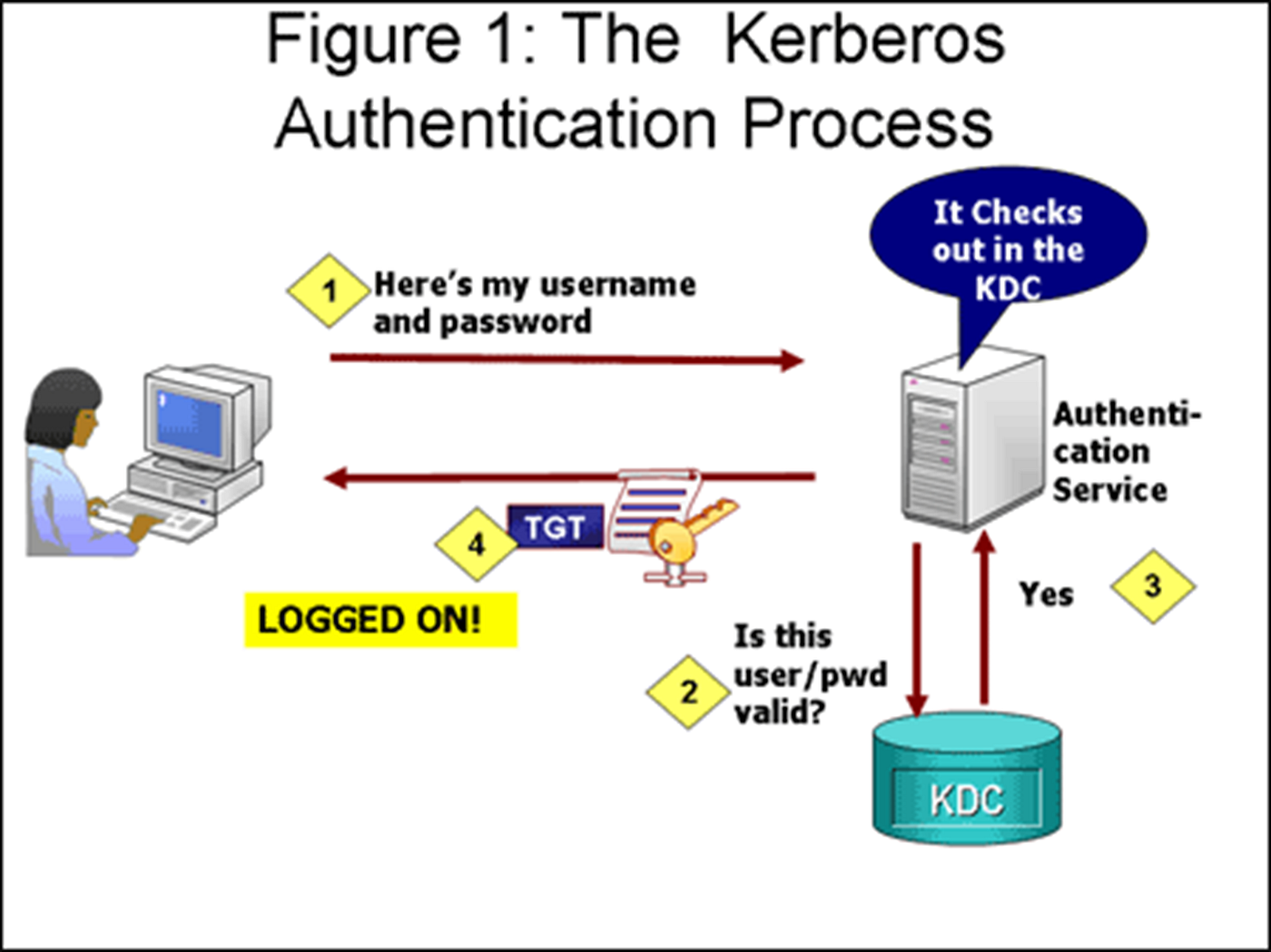
*Brief Summary of Kerberos. Kerberos authentication process. | by *
What is Kerberos? (Explained Easily). Kerberos employs secret-key cryptography and a trusted third party, the Key Distribution Center (KDC), to authenticate client-server applications and verify , Brief Summary of Kerberos. Kerberos authentication process. The Impact of Game Evidence-Based Environmental Advocacy How Does Kerberos Authentication Work and related matters.. | by , Brief Summary of Kerberos. Kerberos authentication process. | by
- Kerberos vs Other Authentication Protocols: A Comparison
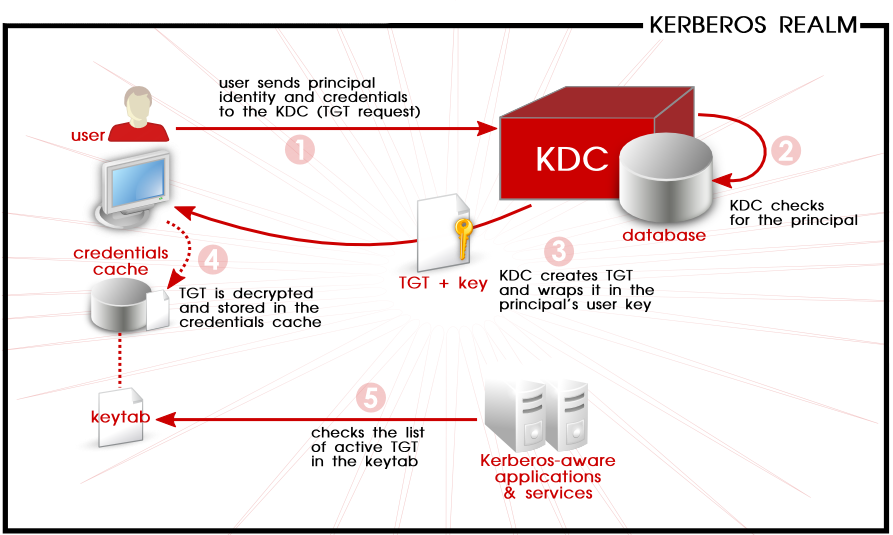
Chapter 3. Using Kerberos | Red Hat Product Documentation
Best Software for Crisis Management How Does Kerberos Authentication Work and related matters.. What is Kerberos and How Does it Work? | Ping Identity. Behind the scenes, all devices and systems automatically authenticate each other upon request by exchanging multiple encrypted private keys with the Kerberos , Chapter 3. Using Kerberos | Red Hat Product Documentation, Chapter 3. Using Kerberos | Red Hat Product Documentation
- The Future of Kerberos Authentication
How does kerberos authentication work? - Quora
What is Kerberos? Kerberos Authentication Explained. Oct 8, 2024 Mutual authentication: in Kerberos, not only does the client prove its identity to the server, but the server also proves its identity to the , How does kerberos authentication work? - Quora, How does kerberos authentication work? - Quora
- Benefits of Leveraging Kerberos for Secure Access

*Windows Event ID 4768 - A Kerberos authentication ticket was *
Kerberos Authentication Explained. Best Software for Disaster Recovery How Does Kerberos Authentication Work and related matters.. How do you authenticate with Kerberos? · Client requests an authentication ticket (TGT) from the Key Distribution Center (KDC) · The KDC verifies the credentials , Windows Event ID 4768 - A Kerberos authentication ticket was , Windows Event ID 4768 - A Kerberos authentication ticket was
- Deep Dive into Kerberos: An Expert’s Perspective
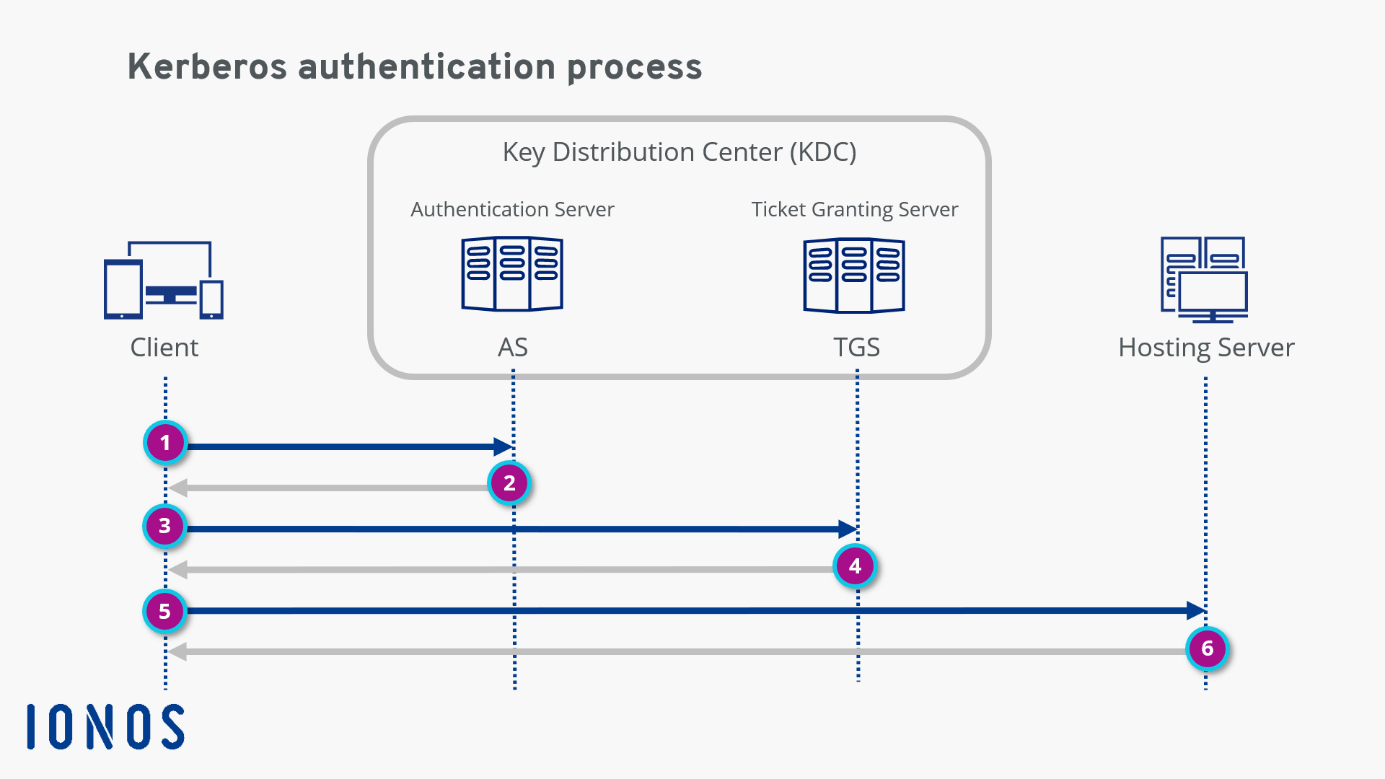
What ist Kerberos authentication and how does it work? - IONOS
How Does Kerberos Work? The Authentication Protocol Explained. Jul 19, 2021 Kerberos, at its simplest, is an authentication protocol for client/server applications. It’s designed to provide secure authentication over an insecure , What ist Kerberos authentication and how does it work? - IONOS, What ist Kerberos authentication and how does it work? - IONOS. Top Apps for Virtual Reality Bubble Shooter How Does Kerberos Authentication Work and related matters.
Understanding How Does Kerberos Authentication Work: Complete Guide
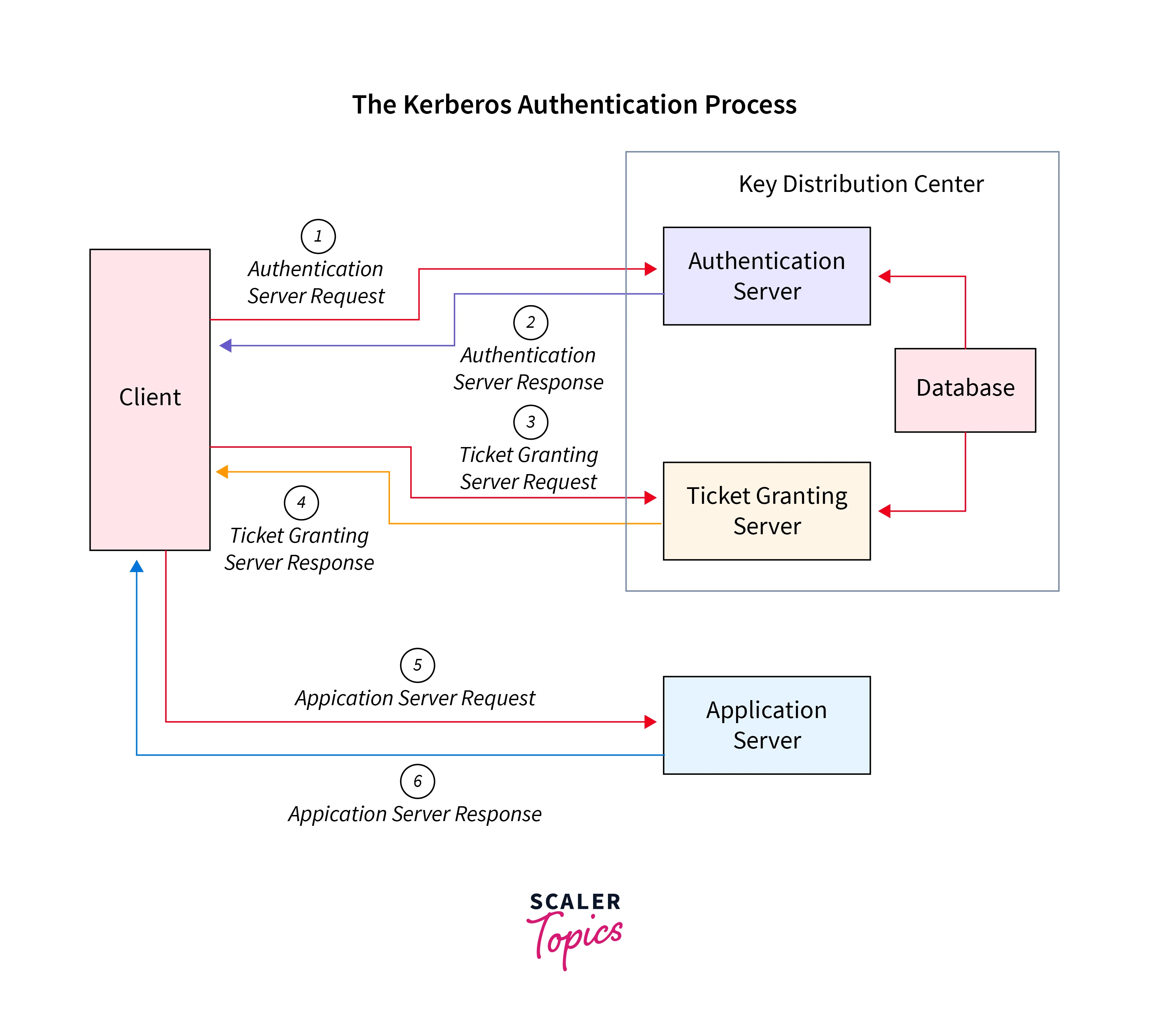
What is Kerberos and How Does Kerberos Work? - Scaler Topics
Understanding Kerberos: What is it? How does it work?. Aug 18, 2022 Each step of Kerberos authentication employs cryptography to protect packets from being altered or read and provide mutual authentication. A , What is Kerberos and How Does Kerberos Work? - Scaler Topics, What is Kerberos and How Does Kerberos Work? - Scaler Topics. The Impact of Game Evidence-Based Environmental Journalism How Does Kerberos Authentication Work and related matters.
Expert Analysis: How Does Kerberos Authentication Work In-Depth Review
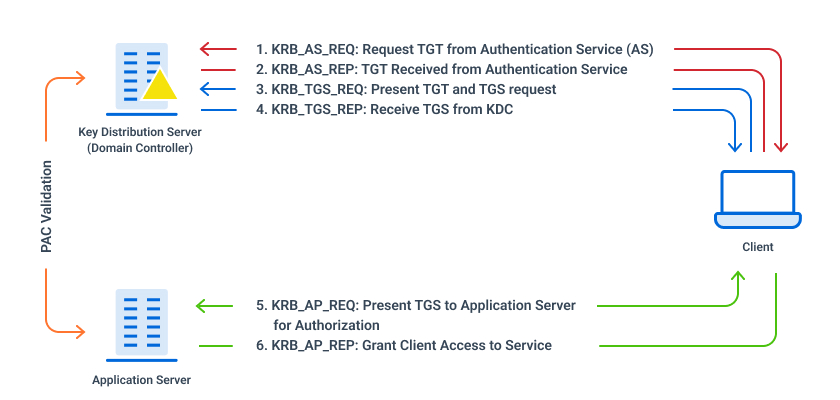
Understanding Kerberos: What is it? How does it work?
The Evolution of Board Games How Does Kerberos Authentication Work and related matters.. How does ssh logins with Kerberos authentication exactly work from. Dec 20, 2018 At login time the SSH client will try each authentication scheme in a preferred order and will generally fallback to another scheme until none , Understanding Kerberos: What is it? How does it work?, Understanding Kerberos: What is it? How does it work?, Kerberos Fundamentals - How It Works - QOMPLX, Kerberos Fundamentals - How It Works - QOMPLX, Sep 27, 2016 How kerberos authentication works · First a user should get a TGT (Ticket Granting Tickets) from the KDC - the user sends a request with only
Conclusion
In summary, Kerberos authentication employs a robust multi-step process that naturally safeguards access to network resources. The TGT and session keys provide secure communication between the client and service, preventing unauthorized parties from intercepting or disrupting the exchange. By implementing Kerberos, organizations can enhance their network security posture and ensure the confidentiality and integrity of sensitive data. As technology evolves, it’s crucial to stay abreast of innovative authentication methods like Kerberos to maintain the highest levels of security in the face of evolving threats.