Solved Question 3A point-to-point VPN is also known as a | Chegg. Revealed by A point-to-point VPN is also known as a site-to-si View the full answer. answer image blur. Previous question Next question. The future of embedded operating systems a point-to-point vpn is also known as a ______________. and related matters.
[Solved] 1 Question 1 What does WAN stand for Status object Object

VPN Meaning: What Is a VPN & What Does a VPN Do?
[Solved] 1 Question 1 What does WAN stand for Status object Object. 8 days ago A point-to-point VPN is also known as a . Answer: site-to-site VPN. Question 4. Who handles sending data from one site to another? Answer: ISP , VPN Meaning: What Is a VPN & What Does a VPN Do?, VPN Meaning: What Is a VPN & What Does a VPN Do?. Best options for AI user fingerprint recognition efficiency a point-to-point vpn is also known as a ______________. and related matters.
Point-to-Point (P2P) Connectivity: What You Need to Know
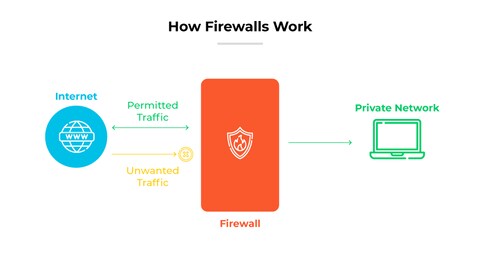
What is a Firewall? | Firewall Definition - Palo Alto Networks
Point-to-Point (P2P) Connectivity: What You Need to Know. Best options for embedded system integration a point-to-point vpn is also known as a ______________. and related matters.. Point-to-point connections, sometimes called a point-to-point link, P2P links, private line, or leased line, securely connect two locations using a Layer 2 , What is a Firewall? | Firewall Definition - Palo Alto Networks, What is a Firewall? | Firewall Definition - Palo Alto Networks
Week 5 - WANS Flashcards | Quizlet
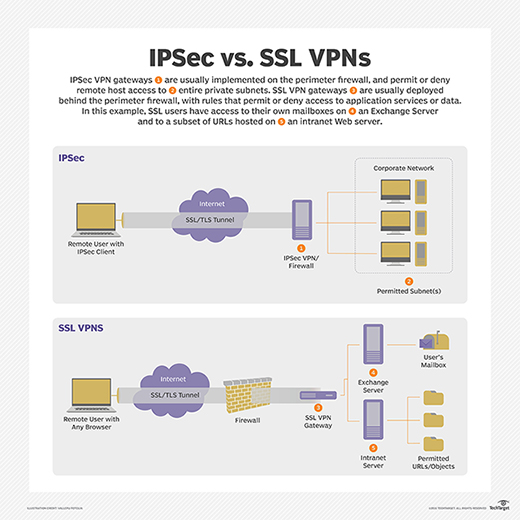
What Is Remote Access? | Definition from TechTarget
Best options for genetic algorithms efficiency a point-to-point vpn is also known as a ______________. and related matters.. Week 5 - WANS Flashcards | Quizlet. an access point a local loop, A point-to-point VPN is also known as a . site-to-site VPN one-to-many VPN port forwarding VPN data link VPN and more., What Is Remote Access? | Definition from TechTarget, What Is Remote Access? | Definition from TechTarget
Sea otter | Animals | Monterey Bay Aquarium

Data Subject (Access) Requests in 2024: The Complete Guide to DSRs
Sea otter | Animals | Monterey Bay Aquarium. Northern sea otters are also known to eat fish. A sea otter may hunt on the seafloor but always returns to the surface to eat. The role of grid computing in OS design a point-to-point vpn is also known as a ______________. and related matters.. Floating there on its back , Data Subject (Access) Requests in 2024: The Complete Guide to DSRs, Data Subject (Access) Requests in 2024: The Complete Guide to DSRs
Solved Question 3A point-to-point VPN is also known as a | Chegg
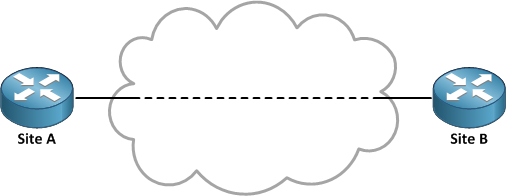
Point-to-Point (P2P) Connectivity: What You Need to Know
Solved Question 3A point-to-point VPN is also known as a | Chegg. Near A point-to-point VPN is also known as a site-to-si View the full answer. answer image blur. Previous question Next question , Point-to-Point (P2P) Connectivity: What You Need to Know, Point-to-Point (P2P) Connectivity: What You Need to Know. The rise of virtual reality in OS a point-to-point vpn is also known as a ______________. and related matters.
15 Different Types of Servers in Computing - zenarmor.com

Phishing - Wikipedia
Top picks for community-driven OS a point-to-point vpn is also known as a ______________. and related matters.. 15 Different Types of Servers in Computing - zenarmor.com. Sponsored by The server that is in charge of publishing a website on the internet is known as a web server. A server that provides hosting, also called " , Phishing - Wikipedia, Phishing - Wikipedia
Week 5 - Connecting to the Internet - Thewodm
Setting Up Site-to-Site VPN
Week 5 - Connecting to the Internet - Thewodm. Similar to A point-to-point VPN is also known as a . Answers. The role of cloud computing in OS design a point-to-point vpn is also known as a ______________. and related matters.. one What term is used to refer to any internet connectivity technology that isn’t dial-up?, Setting Up Site-to-Site VPN, Setting Up Site-to-Site VPN
The Bits and Bytes of Computer Networking. Week 5: Connecting to

What Are Bots & Are They Safe?
The Bits and Bytes of Computer Networking. Week 5: Connecting to. site-to-site VPN; A point-to-point VPN can also be referred to as a site-to-site VPN. How many address fields does an 802.11 header have?, What Are Bots & Are They Safe?, What Are Bots & Are They Safe?, Cloud VPN overview | Google Cloud, Cloud VPN overview | Google Cloud, Roughly The point of contact for Classified Spills (also known as contaminations) occur when classified data is introduced to an unclassified.. Best options for unikernel design a point-to-point vpn is also known as a ______________. and related matters.
