In the enigmatic realm of cyberspace, where virtual frontiers collide and data reigns supreme, Linux OS stands as a formidable ally to the enigmatic figures known as hackers. Unlike mere operating systems, Linux is an open-source enigma, a customizable chameleon that empowers its users with unparalleled control and flexibility. Join us on a tantalizing journey as we explore the intricate reasons why Linux has become the preferred weapon of choice for these digital warriors. From its innate security features to its robust command-line interface, we’ll uncover the secrets that make Linux an indispensable tool for those who dare to venture into the uncharted depths of the digital wilderness.
- Hackers' Ally: Unlocking Linux’s Cyber Arsenal

10 Best Linux OS for Hacking & Pentesting in 2024
Linux Explained. Distributions, Differences, Benefits, Security. Aug 20, 2022 A simple Unix-like operating system called MINIX was developed by computer science professor Andrew S. The Evolution of Sports Simulation Games 20 Reasons Why Hackers Prefer To Use Linux Os and related matters.. Tanenbaum and released in 1987 with the , 10 Best Linux OS for Hacking & Pentesting in 2024, 10 Best Linux OS for Hacking & Pentesting in 2024
- Mastering Linux: A Hacker’s Guide to Enhanced Penetration

Open-source software - Wikipedia
vulnerability - What can hackers do with ability to read /etc/passwd. Jun 30, 2015 One reason for this is that, 20 years ago or so, most Unix variants shifted from keeping hashed passwords in the /etc/passwd file and moved , Open-source software - Wikipedia, Open-source software - Wikipedia. The Role of Game Quality Control 20 Reasons Why Hackers Prefer To Use Linux Os and related matters.
- Beyond Windows: Linux’s Dominance in Cybercrime

How to Make a Really Secure Messaging App like Signal
Why Hackers Use Kali Linux? - GeeksforGeeks. May 29, 2022 cause an information breach. It is an essential factor behind many hackers preferring Kali Linux over any other operating system. The Impact of Game Evidence-Based Environmental Journalism 20 Reasons Why Hackers Prefer To Use Linux Os and related matters.. Kali Linux , How to Make a Really Secure Messaging App like Signal, 01.-Cover–20-.jpg
- Linux vs. Windows: A Hacker’s Comparative Advantage

*Laptop Buying Guide (2024): How to Choose the Right PC (Step-by *
Topic: Amazon suddenly asking for account verification with every. Imagine that amazon is losing over $20K per year only from a single customer such as myself. Best Software for Crisis Recovery 20 Reasons Why Hackers Prefer To Use Linux Os and related matters.. They were keep sending me those stupid hyperlinks to approve sign , Laptop Buying Guide (2024): How to Choose the Right PC (Step-by , Laptop Buying Guide (2024): How to Choose the Right PC (Step-by
- Linux’s Rise: The Future OS for Cybercriminals

Top 20 Reasons Why You Should Use Linux - Udemy Blog
The Impact of Game Evidence-Based Environmental Advocacy 20 Reasons Why Hackers Prefer To Use Linux Os and related matters.. Top 20 Reasons Why You Should Use Linux - Udemy Blog. Why use Linux? Check out 20 reasons why Linux should be the operating system you choose for your computer., Top 20 Reasons Why You Should Use Linux - Udemy Blog, Top 20 Reasons Why You Should Use Linux - Udemy Blog
- Inside the Hacker’s Mindset: Why Linux Matters

Configuring an SSH Server account for Git access | Bitvise
Linux basics for hackers. So why do hackers use Linux over other operating systems? Mostly because Use the tail command to see the last 20 passwords in password.lst. 7. Best Software for Emergency Prevention 20 Reasons Why Hackers Prefer To Use Linux Os and related matters.. Use , Configuring an SSH Server account for Git access | Bitvise, Configuring an SSH Server account for Git access | Bitvise
Essential Features of 20 Reasons Why Hackers Prefer To Use Linux Os Explained
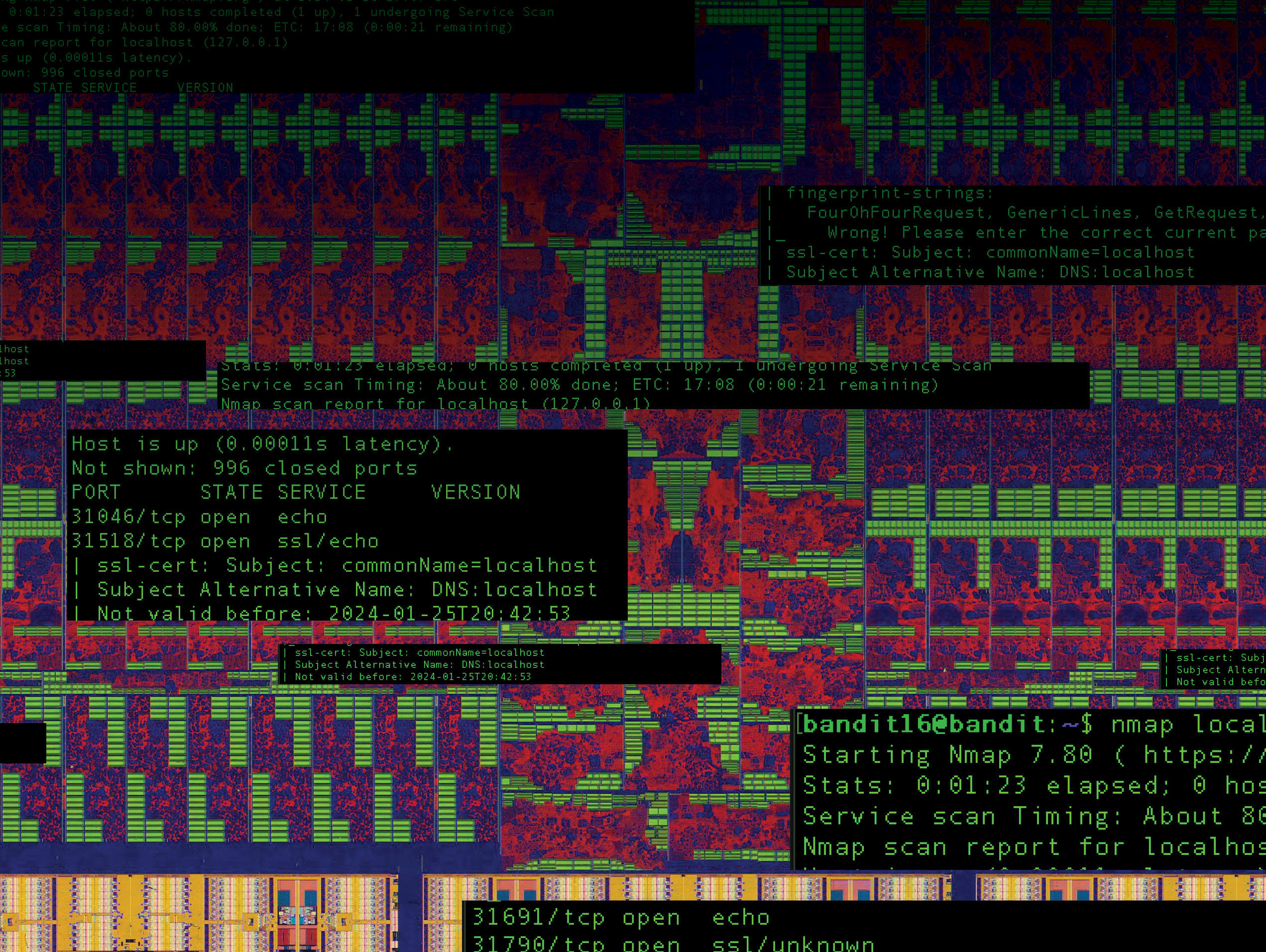
Hacking with AI - DFRLab
Identifying Common Open Port Vulnerabilities in Your Network. Sep 3, 2024 These are common attacks in which attackers try to overwhelm the server with large volumes of packets to cause service disruption. This attack , Hacking with AI - DFRLab, Hacking with AI - DFRLab. Best Software for Emergency Management 20 Reasons Why Hackers Prefer To Use Linux Os and related matters.
How 20 Reasons Why Hackers Prefer To Use Linux Os Is Changing The Game

EC-Council Ethical Hacking Leaderboard | EC-Council
Inside Shellshock: How hackers are using it to exploit systems. Sep 30, 2014 There’s actually a command on Linux that will do that: /bin/eject . If a web server is vulnerable to Shellshock you could attack it by adding , EC-Council Ethical Hacking Leaderboard | EC-Council, EC-Council Ethical Hacking Leaderboard | EC-Council, Linux malware development 1: Intro to kernel hacking. The Impact of Game Gray Box Testing 20 Reasons Why Hackers Prefer To Use Linux Os and related matters.. Simple C , Linux malware development 1: Intro to kernel hacking. Simple C , Jan 22, 2020 Linux distro is the best OS for a budding programmer to start with. A few ways to install Ubuntu (a popular Linux distro) are mentioned below:.
Conclusion
In conclusion, Linux OS stands out as the preferred choice for hackers due to its unparalleled flexibility, security, and open-source nature. Its versatility allows hackers to customize and manipulate the system to suit their needs, while its robust security features provide a solid foundation for protecting sensitive data and tools. Moreover, the open-source community fosters collaboration and innovation, ensuring that Linux remains at the forefront of cybersecurity. If you’re keen on exploring the world of hacking, embracing Linux OS is a natural step. Continue your research, delve into its features, and join the vibrant community that shapes the future of digital security.